The United States Social Security Number
Make no mistake about it, the Social Security Number for every US Citizen is a numbering code for human beings. For all it's intent & purposes, it is a national numbering system that the federal government uses to seek information on every citizen. Perhaps the most disturbing abuse of the Social Security Number is the congressional authorized rule to force parents to get numbers for their new born children in order to claim them as dependents. This is not a isolated incident. In fact, since the creation of the Social Security Number in 1934, there have been almost 40 congressional authorized uses of the number as a identification number for non-Social Security programs. In many states, no one can not get a job, a driver's license, or receive a copy of their birth certificate without first presenting their Social Security Number to government or state agency. This entity, which I call "Big Brother" is slowly taking away our freedom, privacy and civil rights.
The National Security Act
2004 NOV: Since the end of World War II, each administration has sought to develop and perfect a reliable set of executive institutions to manage national security policy. Each President has tried to avoid the problems and deficiencies of his predecessors' efforts and install a policy making and coordination system that reflected his personal management style. The National Security Council (NSC) has been at the center of this foreign policy coordination system, but it has changed many times to conform with the needs and inclinations of each succeeding chief executive. The National Security Act of 1947 mandated a major reorganization of the foreign policy and military establishments of the U.S. Government. The act created many of the institutions that Presidents found useful when formulating and implementing foreign policy, including the National Security Council (NSC). The act also established the Central Intelligence Agency (CIA), which grew out of World War II era Office of Strategic Services and small post war intelligence organizations. The CIA served as the primary civilian intelligence gathering organization in the government. Later, the Defense Intelligence Agency became the main military intelligence body. The President's Special Counsel, complained about "the failure of the bill to define in clear terms the sense in which the word intelligence' is used. For example, 'intelligence,' 'foreign intelligence,' 'intelligence relating to the national security,' 'strategic and national policy intelligence,' 'the national intelligence mission,' and 'intelligence affecting the national security,' are used indiscriminately as though they were synonymous." The failure to distinguish between 'intelligence' and 'foreign intelligence'" would "lead to the suspicion that the 'National Intelligence Authority' and the 'Central Intelligence Agency' and The FBI will attempt to gain control, with the powers granted to them.
The Joint Chiefs of Staff plan clearly envisaged a Presidential directive; the McCormack plan appeared to do so; and when the Secretaries of State, War, and Navy reached agreement in January 1946, they also recommended action by Presidential directive. Secretary of State Byrnes apparently believed that the Reorganization Act of 1945 gave the President the authority he required and needed for the necessary authority and standing to develop, support, coordinate and direct an adequate Federal intelligence program. Ever cautious about separate legislation on intelligence, the White House drafted the armed forces unification bill included the establishment of a Central Intelligence Agency as one of its provisions. The White House continued to fear that a Central Intelligence Agency might prove controversial in the Congress and resisted efforts to expand the scope of the bill, hoping to keep the intelligence provisions as inconspicuous as possible and preferring that more detailed enabling legislation be submitted to Congress at a later date. The National Security Act of 1947 entered into force on September 19, 1947, and the Central Intelligence Agency came into being as a statutory body the next day. In creating the National Security Council, the National Security Act of 1947 provided the President with an invaluable forum for the consideration and coordination of domestic, foreign, and military policies related to America's security. In 1997, President Clinton of the United States of America, proclaimed September 14 through September 20, 1997, as a time to commemorate the 50th Anniversary of the National Security Act of 1947.
The Patriot Act In the last decade we have witnessed an enormous explosion in the amount of tracking and information of individuals in the United States. The explosion of computers, cameras, location sensors, wireless communication, biometrics, and other technologies is making it a lot easier to track, store, and analyze information about a individuals' activities. The law enforcement publication POLICE MAGAZINE published an article in their May-June 2004 issue in which The 5th United States Circuit Court has ruled that law enforcement officers are not required to obtain a search warrant prior to investigating a business or residence. This new decision was handed down in accord concerning the 1994 case of United States vs. Kelly Gould. The majority of the American population are not even aware of these laws that attack their freedoms. It took only 45 days after the September 11 attacks, and with virtually no debate, Congress passed the THE PATRIOT ACT. Many parts of this sweeping legislation take away the checks on law enforcement and threaten the very rights and freedoms that we are struggling to protect. For example, without a warrant and without probable cause, the FBI now has the power to access your most private medical records, your library records, and your student records. A veil of secrecy has shrouded the Patriot Act for years. Among the other documents released by the FBI is an e-mail that acknowledges that Section 215 can be used to obtain physical objects, in addition to records. It states the FBI could use Section 215 to obtain a person's apartment key. The Attorney General has previously acknowledged that Section 215 can be used to obtain computer files and even genetic information. Another document released by the FBI is an internal FBI memo, dated October 29, 2003, acknowledging that Section 215 of the Patriot Act can be used to obtain information about innocent people. The memo contradicts the governments assertion, made repeatedly on the public record, that Section 215 can be used only against suspected terrorists and spies. "It is remarkable that the government never made any effort to inform the plaintiffs or even the Court that it has begun using Section 215," said Ann Beeson, Associate Legal Director of the ACLU. Below are a few examples of The Patriot Act : Sec. 215. Access to records and other items under the Foreign Intelligence Surveillance Act.
Sec. 326. Verification of identification.
Sec. 351. Amendments relating to reporting of suspicious activities.
Sec. 405. Report on the integrated automated fingerprint identification system for ports of entry and overseas consular posts.
Subtitle Enhanced Immigration Provisions Sec. 416. Foreign student monitoring program. Sec. 503. DNA identification of terrorists and other violent offenders. Sec. 507. Disclosure of educational records.
The key to these law definitions is that their is no key. It's wording and it's meaning can be interrupted in numerous fashions. One example is what and whom are terrorists? What defines a terrorist ? One example, according to The Bush administration, is that a computer hacker is defined as a terrorist. My conclusion is that this type of government agenda reminds me of the Nazi mentality in the 1930s where the Nazi Party encouraged it's citizens to report suspicious activities being committed by their neighbors, their family, or fellow workers. The outcome led to the banning of all commerce and the rights of the jewish citizen, which led to Hitler's final solution according to his fascist views of "the jewish problem", known as the Holocaust, where millions of jewish origin and other citizens were murdered in the Nazi concentration camps in World War II. The similarities of The Patriot Act and The Third Reich are frightening due to their similar doctrine and the way both ideologies were born, and then made into law. The Domestic Security Enhancement Act (also called “Patriot Act 2”) Further dismantles court review of surveillance, such as terminating court approved limits on police spying on religious and political activity. It allows the government to obtain credit records and library records secretly and without judicial oversight. Allows wiretaps without a court order for up to 15 days following a terrorist attack Allows government to operate in secret by authorizing secret arrests, and imposing severe restrictions on the release of information about the hazards to the community posed by chemical and other plants. Patriot Act II further expands the reach of an already over broad definition of terrorism so that organizations engaged in civil disobedience are at risk of government wiretapping. The 2005 exposure of CIA ran concentration camps for suspected terrorist were being operated in countries outside of US legal jurisdiction on purpose. Torture and murder are being used in these camps. These are only a few examples. The vagueness and the exploitation of The Patriot Act include: Under the TIA program, every aspect of our lives would be catalogued and made available to government officials.The USA PATRIOT Act, at section 802, provides that any actions, occurring primarily within the United States, are “domestic terrorism” if they;
(1) “involve” a violation of state or federal criminal law. (2) “appear to be intended” to influence government policy or a civilian population by “intimidation or coercion. (3) “involve acts dangerous to human life.”
According to the wording of section 802, an act of littering could be deemed a terrorist act as all states classify littering a criminal offense, thus a violation of state law as portrayed above. The Patriot Act is nothing short of propaganda to invoke a false sense of security, as well as the loss of constitutional and civil rights of citizens and the elimination of judicial process. In April of 2004, The FBI, endorsed by The Department of Justice and the Drug Enforcement Agency submitted a 85 page proposal to the FCC requesting extra wire tapping and monitoring on all forms of Internet Communications. The proposal includes more eavesdropping capabilities on instant messaging, cable modems, DSL, and so forth. The 1994 Communications Assistance for Law Enforcement Act ( The CALEA ) had established rules and legal guide lines for wire tapping telecommunications providers. The report released by the US Justice Department concerning convicted FBI agent Robert Hanssen was a startling revelation on the lax and careless measures committed by the FBI. It showed how a mediocre agent exploited lax security at the agency over a 20 year period. The 31 page report noted the failures and incompetence within the FBI which is almost frightening considering the FBI is the main security entity for American security and intelligence. Inspector General Glenn A. Fine noted a few of the outlandish and stupidity concerning the activities of FBI agent Robert Hanssen, who now sits in prison.
The United States is turning into a full fledged surveillance society leading the human race into a global society of Orwellian surveillance. The tremendous explosion in surveillance enabling technologies, combined with the ongoing weakening in legal restraints that protect our privacy mean that we are drifting toward a surveillance society. "Total Information Awareness" may be the closest thing to a true "Big Brother" program that has ever been seriously contemplated in the United States. TIA is based on a vision of pulling together as much information as possible about as many people as possible into a global database, making that information available to government officials, and sorting through it to try to identify terrorists or civilians whom pose a real or imagined threat to this Big Brother Society. Since the amount of public and private information on our lives is growing by leaps and bounds every week, a government project that seeks to put all that information together is a radical and frightening form of human profiling. TIA is run by the Defense Advanced Research Projects Agency (DARPA), a branch of the Department of Defense that works on military research. TIA would represent a radical departure from the centuries old American tradition that the police conduct surveillance only where there is evidence of involvement in wrongdoing. It would seek to protect us by monitoring everyone for signs of wrongdoing, by instituting a giant dragnet capable of sifting through the personal lives of Americans. It would ruin the very American values that our government is supposed to be protecting the plus lives of our brave men and women in the current Iraq war whom are under the assumption that is what they are fighting. The TIA program is based on highly speculative assumptions about how databases can be used to stop terrorism, and this program in stopping terrorism is highly speculative, but the damage that it would do to American freedom is certain.
The use of computers have revolutionized global crime and has given law enforcement unlimited tools to fight cyber terrorist, even the tools of eliminating any rights, privacy, or judicial process. The United States was once founded on such documents as The Constitution, The Bill of Rights, Civil Rights, and all those other freedoms that US citizens take for granted. Not only have the citizens of The United States lost numerous freedoms, but like a cancer, it is spreading like a virus on a global scale. Americans have the right to expect that their lives will not become an open book when they have not done, and are not even suspected of doing, anything wrong and it harbors a tremendous potential for abuse. The motto of the TIA program is that “knowledge is power,” and in fact the keepers of the TIA database would gain a tremendous amount of power over American citizens. Inevitably, some of them will abuse that power. The government has not been shy about storing information in their data base, and it is envisioned as a primary source for the TIA database. The information that is generated and retained about our activities is becoming so rich that if all that information about us was put together, it would almost be like having a video camera following us around. Programs like TIA make such "data surveillance" a reality in today's global community. The U.S. government knows that the American people will never go for a national I.D. card or a national database of every Americans fingerprints and photographs. But that database theology is already here and being implemented. When did the government ever listen to it's citizens on the matters of privacy. This United States national data base already has details on 100 Million Americans claiming these policies are necessary to comply with international standards. An example of the kind of abuses that can happen were chronicled in a July 2001 investigation by the Detroit Free Press (and December 2001 follow up): the newspaper found that police officers with access to a database for Michigan law enforcement had used it to help their friends or themselves. The officers would threaten motorists, track estranged spouses, and to intimidate political opponents. Another example is J. Edgar Hoover, was notorious for abusing power, black mail, and even keeping American Presidents under his thumb. No one can hold the director of such a powerful agency as the FBI for more than forty years without some sort of hold over others in power. Hoover's abusive and criminal activities which are finally being revealed 20 years later have prompted many legislators to have his name removed from the FBI headquarters in Washington. Experience has shown that when large numbers of Americans challenge the governments policy (for example in Vietnam), some parts of the government react by conducting surveillance and using propaganda against these critics of freedom. The unavoidable truth is that a super database like the TIA will lead us into a One World Government and the surveillance of the human race.
GIS and COMPSTAT and other numerous crime mapping programs have been in use since 1990. The Geographic Information System ( GIS ) uses GPS satellites to analyze and map every square foot of the planet. In short, the Earth is transformed into a digital map. The usefulness of GIS to government law enforcement agencies is that these digital maps can be overlaid with strategic and tactical information as well monitoring and tracking technologies The GIS system was reportedly developed by the New York City Police Department in 1994 which was named COMPSTAT. The COMPSTAT program is a advanced tool for law enforcement to better it's efficiency and accuracy in collecting and documenting evidence, which includes the advance use of biometrics technology. COMPSTAT eventually grew into a nation wide data base for officers to access it, or abuse it. One draw back to this type of investagative tool was it may allow police to intrude on citizens privacy.
On July 4, 1966 President Lyndon Baines Johnson signed into law legislation the Freedom of Information Act ( FOIA) which entitled citizens, reporters, and historians to legally request and obtain copies of government documents, except for those documents that were specifically exempted. The FOIA has proven to be a vital tool in exposing and reporting acts to the public, in which a majority of the public were shocked at the actions and operations the government had committed. Over 6,000 new stories from the year 2002 through 2003 were reported which included the theft of weapons from United States stockpiles, the exposure of germ warfare chemicals on American soldiers in the 1960's, to other covert acts committed by those in governmental and military agencies. The government is making it harder to acquirer requested documents using the old excuse of national security to, as mentioned earlier, documents that were specifically exempted. This phrase " specifically exempted " in theory and under the color of the law, could be translated into that ALL documents could be exempted.
The CIA has enjoyed many years of this operational exempted law and denial of any of it's operations makes them infallible to the law and the Constitution. A good example of such deception would be a 1968 incident in which a Soviet submarine exploded and sunk in the Pacific ocean. The government, wanting to gain the secrets of the Soviet submarine's technology used a specially built vessel, named the Glomar Explorer, to retrieve the sub and it's components in which it was partially successful. The incident was reported by the press but when it asked the CIA for documents under the FOIA, the CIA and the government denied any such operation existed. The CIA claimed that if a incident of this nature even existed, it would be protected by the classified documents that were specifically exempted from the FOIA. Even if the agency was forced to supply the documents, all you would get would be page after page of blacked out lines, information deemed classified or which may pose a threat to national security. This is what makes The Patriot Act such a dangerous law and already those in power are using it too trample the rights and laws that every american citizen are entitled too. And the abuse of this law, which was designed for terrorists, will be used for any operation the government deems justified. The FBI in Las Vegas used a investigation named Operation G-String to go after the cities biggest alleged strip club owner, Michael Galardi. Using The Patriot Act, which gives law enforcement agencies a green card to eavesdrop, wire-tap, even enter a business or home without a search warrant, without any form of judicial process, just do as they please and go after their enemies, real or imagined. As of this story, I don't see how a strip club poses a threat of terrorism. Even when The Patriot Act was passed after the 911 attacks, myself and many others which included civil libertarians, ACLU, claimed and knew this law would be abused. US Attorney General Ashcroft ( American equal of Adolf Hitler ) labeled these people as hysterics and preached that any weakening of The Patriot Act would endanger american lives. Another item of The Patriot Act allows the FBI to monitor the books people check out of public libraries. The Las Vegas FBI labeled Operation G-String lawful and told Shelley Burket, a Nevada Democrat that the investigation was legal and that The FBI was using the tools that Congress gave them. This FBI reply left Shelley Burket asking," When did The Patriot Act deem that our nation be kept safe from strip club owners?" Future abuses of this law will grow and until The American People see the ruthlessness and fallacy of this law, you may be yourself deemed a terrorist associate because you had purchased ice cream from a company that made it is suspected of having terrorists ties.
One World Government.
 The United Nations Assembly Council can be seen as a form of The New World Order & One World Government
The United Nations Assembly Council can be seen as a form of The New World Order & One World GovernmentSince World War II, secret groups of bankers, politicians, and scientists have met regularly to plan the creation of a one world government. These people do not trust democracy because they know the average patriotic American or Canadian would never willingly surrender his country and constitution to be ruled by some faceless foreign leaders on some secret international committee. In the early 1970's Zbigniew Brzezinski, President Carter's National Security Advisor, founded the Trilateral Commission under financial control and direction of David Rockefeller, chairman of the Council on Foreign Relations. His books and confidential reports to these organizations have developed many of the basic strategies of the coming New World Order. Even Albert Einstein was interviewed in The Atlantic Monthly by reporter Raymon Swing in November 1945 and November 1947. Einstein was against giving the secrets of the atomic bomb to the United Nations, but was leaning more to a world government. This world government he stated should be started by the three major military powers of that time which was The United States, Great Britain and the Soviet Union. This new world government would share it's nuclear secrets with the Russians to make them less suspicious, because they had not yet acquired nuclear technology at the time. 
World Trade Bank in Washington D.C.
As a result of Brzezinski's input they developed a more subtle plan that appeared to create a competition between three economic and political super states. However, the hidden reality was the the The United States, Japan, and Germany represented three branches of a global enterprise. The plan required each of the three superpowers to take the first steps to dominate and finally merge the nations in their own area. Public opinion is being persuaded by the media to accept the loss of sovereignty in return for the promised blessing of a stable international, political and economic New World Order. Once this stage is complete the final step will be to merge the three superpowers into a One World Government. On January 30,1976,32 Senators and 92 Representatives signed The Declaration of Inter dependence. This document was an attempt to create propaganda for the the planned New World Order. This was their statement, " Two centuries ago our forefathers brought forth a new nation; now we must join with others to bring forth a new world order. Germany is now conquering the nations of Europe through economic and political means. Japan is rapidly dominating the countries it tried to conquer in World War II and now is forming a new Greater East Asia Co-prosperity Sphere. The United States has created The North American Free Trade Agreement ( NAFTA) to consolidate the economies of Mexico, Canada and America. This Trilateral approach succeeded in creating the impression among many people that there is a true international competition underway between The United States, Europe and Japan.
The One World Bank
World Bank and International Monetary Fund. The International Monetary Fund (IMF) and the World Bank originated during World War II in preparation for postwar international financial and economic cooperation. Initiated by the United States and Great Britain, these efforts culminated in the UN Monetary and Financial Conference held in July 1944 at Bretton Woods, N.H., U.S. Forty-four nations attended the conference, although the resulting system of international postwar reconstruction and monetary relations, known as the Bretton Woods system, was based on liberal principles articulated largely by the United States. The principal functions of the World Bank are to assist in the reconstruction and development of its member countries by facilitating capital investment for productive purposes, to promote private foreign investment by guarantees of and participation in loans and other investments made by private investors, and to make loans for productive purposes out of its own resources or funds borrowed by it when private capital is not available on reasonable terms. The IMF was designed to stabilize international monetary rates and promote foreign exchange cooperation, though its function of extending loans for structural adjustments has increased dramatically. Both agencies have been focal points of contention between the Western industrialized and Third World countries, the former insisting on adherence to market principles and the latter asserting that such adherence causes undue hardships for developing states. The primary focus of these agencies has shifted from the advanced industrialized countries to Third World states owing to successful postwar reconstruction in the West, decolonization, and difficulties in development in the Third World that were exacerbated by the oil shocks of the 1970s. Both agencies are powerful players on the international economic scene.
The World Bank encompasses three separate institutions: the International Bank for Reconstruction and Development (IBRD), which is its most important component; the International Development Association (IDA); and the International Finance Corporation (IFC). Twenty-nine nations signed its articles of agreement in 1945. By the early 1990s the bank had more than 160 members. The bank is governed by an executive board and a managing director. Voting in the bank is weighted according to initial contributions to the bank's capital. The World Bank may lend funds directly, guarantee loans made by others, or participate in such loans. Loans may be made to member countries directly or to any of their political subdivisions or to private business or agricultural enterprises in the territories of members. The World Bank obtains its funds for loans primarily from borrowings in the capital markets. Its soft-loan component, the IDA (established in 1960), lends to low income countries on more favorable terms, free of interest except for a small service charge. The IFC (established in 1956) provides loans to private business in developing countries.
Most of the World Bank's loans in its early years underwrote large-scale infrastructure projects--roads, railways, ports, power facilities, and telecommunications. Since about 1970 an increasing proportion of World Bank lending has been for agricultural, educational, and population programs in the Third World. Many programs have met with little or mixed success in their goal of pulling developing states out of poverty and increasing self-sufficiency, and so have engendered controversy. Furthermore, the bank's lending was further complicated in the 1980s by the world debt crisis and the fact that many debt-plagued states fell behind in loan repayments. The World Bank has, more recently, committed itself to sector assistance for farmers and business entrepreneurs as well as to projects that meet the environmental criteria outlined by the UN Environment Program.
The IMF came into existence in December 1945, but its first transactions were not made until 1947. It is administered by a board of governors and 22 executive directors. Member governments subscribe the IMF's operating funds. Each member has a quota based on a formula that includes its GNP, reserves, and trade potential and pays its quota in its own currency or with a mix of its currency and acceptable reserve assets, including " special drawing rights" (or SDRs), which allow a country to purchase currency for other transactions. A member's quota determines both its voting power in the agency and access to funds. Members may arrange standby credits to use as and if necessary. The IMF has created a number of "facilities" under which it provides loans to countries facing particular difficulties. The expansion of world trade, coupled with a succession of international financial crises, created a demand for additional reserves that could be used in the settlement of international balances. In 1971, as a result of these crises, the U.S. dollar went off the gold standard, marking the formal end of the Bretton Woods monetary system. By March 1973, a system of generalized floating had taken its place and is still used today. As a result, the IMF no longer intervened to stabilize monetary relations in currency crises; rather, its attention since the 1970s has been focused on the world debt crisis. (see also Index: international trade, floating exchange rate)
The IMF's lending has been intended to be for short-term purposes. In practice, this has worked more effectively for advanced countries, which formed the bulk of IMF recipients until the late 1960s, than for developing countries, which applied for funds in increasing numbers after the oil crisis of 1973. Many developing countries have become dependent on IMF loans, given uncertain export markets, the high cost of imports, and preexisting heavy debt burdens to both the IMF and private banks. Moreover, IMF conditionally, whereby the agency insists on certain measures of structural adjustment before approving loans, has generated controversy between the advanced industrial states, which wield the greatest voting power in the agency, and Third World states, which apply for loans. IMF conditions may include provisions for lifting foreign exchange restrictions and price controls, liberalizing trade, and cutting spending to balance budgets. In imposing these conditions, the IMF wields considerable influence on the domestic economic policies of the states that apply for assistance. Despite the relatively strict conditions often attached to loans, membership in the IMF has increased over the years, and loans were extended to Russia and a number of eastern European states after the end of the Cold War.
The United Nations

The United Nations ( UN) was formed during World War II by the allied nations in hope that it could be used to prevent another disastrous world war. However, in the past five decades 1945-1998 more than 37 million people were killed in over 340 wars. While we talk about peace, the world still arms for Armageddon. Despite the collapse of The Soviet Union, six hundred major Russian arms factories are running 24 hours a day. Despite the talk of peace there is a greater threat of war today than any other time since 1945. The United Nations was founded on the basis of respect for the individual sovereignty of each member nation. A fundamental principle of the UN was that the international body would never interfere in the internal affairs of a sovereign member nation. However, with the collapse of the Soviet Union and the growing support for a New World Order this principle of non-interference has eroded to the point of extinction. As an example, following the Gulf War, the UN massively intervened in Iraq's internal affairs to carve out an enclave to protect the Kurdish minority in northern Iraq from the armed attacks of Saddam Hussein.
The New York Times published an article entitled "The New World Army" in March, 1992, calling for the creation of a permanent UN army. The bill for 11 UN peacekeeping missions involving 77,000 blue helmeted UN troops could exceed 3.7 billion dollars. As demands grow for a permanent UN rapid deployment army, negotiations have commenced to include Russia, European, Canadian, and American Special Forces in the core of the future New World Army. One of the most dangerous things about the UN Charter and various other international treaties is that they literally supersede the constitutions of our democratic countries. As an example, the US Constitution states that treaties signed by the Senate supersede our own Constitution. There fore, if there is a conflict between a UN treaty and the laws of the Untied States, the Supreme Court will demand that the government obey the dictates of The United Nations treaty. The United Nations maintains its headquarters in New York City. It also has offices in Geneva and Vienna and operates field stations in other cities around the world. The United Nations (UN) became the successor to the League of Nations and absorbed much of the latter's administrative and physical apparatus when it was disbanded in 1946. The United Nations formed a continuum with the League in general purpose, structure, and functions; many of the United Nations' principal organs and related agencies were adopted from similar structures established earlier in the century. In some respects, however, the United Nations constituted a very different organization from the League, especially with regard to the objective of maintaining international peace and security. Differences with the League were due to changes incorporated into the UN's decision making apparatus and to changes in the nature of international relations. Cold War tensions between the United States and the Soviet Union (until its dissolution in 1991-92) deeply affected the security functions of the United Nations during its first 45 years, while extensive post-World War II decolonization in Africa, Asia, and the Middle East increased the volume and nature of political, economic, and social issues that confronted the organization. Finally, the end of the Cold War in 1990 brought renewed attention and appeals to the United Nations, posing challenges to established practices and functions, especially in the areas of conflict resolution and humanitarian assistance, in the midst of an increasingly volatile geopolitical climate.
International organization established by charter on Oct. 24, 1945, with the purposes of maintaining international peace and security, developing friendly relations among nations on the principle of equal rights and self-determination, and encouraging international cooperation in solving international economic, social, cultural, and humanitarian problems. The term United Nations was originally used during World War II to denote those countries that were allied against the Axis powers (Germany, Japan, and Italy). A conference at Dumbarton Oaks, an estate in Washington, D.C., was the earliest attempt to permanently establish this United Nations. Representatives of the "Big Four" (United Kingdom, United States, U.S.S.R., and China) met there from Aug. 21 to Oct. 7, 1944, to draft some preliminary proposals, which were later discussed and more clearly outlined at the Yalta Conference in February 1945 by the Allied war leaders Winston Churchill, Joseph Stalin, and Franklin D. Roosevelt. The proposals, supplemented by these three leaders' decisions, formed the basis of negotiations at the United Nations Conference on International Organization, held in San Francisco two months later; the resultant Charter of the United Nations was signed in June and came into force on Oct. 24, 1945. The United Nations' headquarters is now located at the UN Building in New York City. Six principal organs of the United Nations were established.
The General Assembly (q.v.) includes representatives of all members of the UN. A nation may send up to five representatives but still has only one vote. Decisions are reached either by majority or by two-thirds vote, depending upon the subject matter. The General Assembly works through the committee system and receives reports from the various councils. It performs such functions as supervising trust agreements, budgetary matters, and financial assessments. The assembly elects judges to the International Court of Justice and plays an important role in amending the UN's charter and proposing conferences. It is convened yearly or by special session when necessary.
The Security Council (q.v.) consists of 5 permanent members--United States, Russia (until 1991, the U.S.S.R.), United Kingdom, France, and China--and 10 non permanent members (6 until 1965). The council functions continuously and is mainly concerned with the maintenance of international security. The presidency is rotated among members each month. Non permanent members are chosen from groups and regions in the most equitable fashion possible. Nine votes (including those of all five permanent members) are sufficient to carry a Security Council decision, but any permanent member may exercise a veto over any substantive proposal.
The Economic and Social Council (q.v.) is mainly concerned with the management of the UN's social, economic, cultural, and humanitarian activities. Convening at least twice yearly, this council conducts studies and proposes suggestions for economic and social improvements. The council oversees many commissions, including four major ones in Europe, Asia, Latin America, and Africa.
The International Court of Justice (q.v.), also known as the World Court, is located in The Hague. It is the main judicial branch of the UN and consists of 15 judges elected for nine-year terms by both the General Assembly and the Security Council. Each judge must come from a different country. The court settles disputes and hands down decisions and opinions to the General Assembly and the Security Council. [Table]
The Secretariat (q.v.) is the administrative department of the UN, headed by the secretary-general, who functions in a position of political importance and is appointed for a five-year term by both the General Assembly and the Security Council. (see also Index: Secretariat)
The United Nations attempts to promote harmonious interaction among the countries of the world. The UN has sometimes used peacekeeping forces to halt fighting in or between various countries. (The UN peacekeeping forces were awarded the Nobel Peace Prize in 1988.) Other programs and agencies under the UN's supervision include the International Bank for Reconstruction and Development (World Bank); International Monetary Fund (IMF); International Labour Organization (ILO; recipient of the 1969 Nobel Peace Prize); Food and Agriculture Organization (FAO); World Health Organization (WHO); United Nations Educational, Scientific and Cultural Organization (UNESCO); and United Nations Children's Fund (UNICEF; recipient of the 1965. Like the League of Nations before it, the United Nations is concerned with issues of human rights, including the rights of women and children, refugee resettlement, and narcotics control. Some of its greatest successes have been in the area of improving the health and welfare of the world's population.
 The New World Order
The New World OrderBoth the short comings and the limited practicability of all the approaches to the elimination of war through the reform of the international system have driven many thinkers to accept the idea that war can only be abolished by a full scale world government. No midway solution between the relative anarchy of independent, individual states and a world government with the full paraphernalia of legislative powers and of an overwhelming military force would provide a sufficiently stable international framework for the nations to feel that wars would not break out and thus stop them from behavior that is often conducive to wars. In an age faced with the danger of a war escalating into a general extermination of mankind, the central importance of preserving peace is obvious and is generally accepted. But here the thinkers divide. Some press on from this analysis to the logical conclusion that mankind must, and, therefore, will establish a world government, and they advance ideas how best to proceed in this direction. Others regard the world government as completely utopian, no matter how logical and desirable it may be. Yet, in terms of actual policies, the adherents of the two schools do not necessarily divide. Whether they do or do not believe that world government is attainable, they do agree that the complex phenomenon of war represents a potential calamity of such a magnitude that all theorists must endeavor to understand it and to apply their understanding to the prevention and mitigation of war with all the means at their disposal.
MODERN MONETARY SYSTEMS
Monetary systems are today very much alike in all the major countries of the world. They consist of three levels: (1) the holders of money (the "public")--individuals, businesses, governmental units; (2) commercial banks (privately or governmentally owned), which borrow from the public and make loans to individuals, firms, or governments; and (3) central banks, which have a monopoly on the issue of certain types of money, serve as the bankers for the central government and the commercial banks, and have the power to determine the quantity of money. Time Magazine's April 1998 Cover explained about the new Debit card in which all money transactions and information on you will be stored on a computer chip debit card. 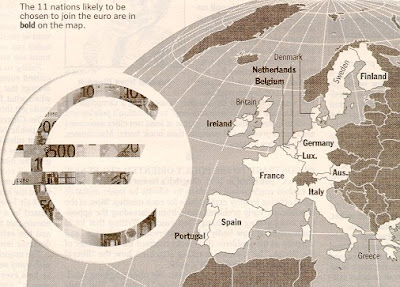
The New Euro Dollar Nations.The beginning of the reunification of the Roman Empire.
EUROPEAN COMMUNITY-REBIRTH OF THE ROMAN EMPIRE
 Jacque Delors and, Past Current President Santer Jacques of The ECC which resides on the 13th floor of the Berlaymont, the enourmoud headquarters in Brussels Belgium.
Jacque Delors and, Past Current President Santer Jacques of The ECC which resides on the 13th floor of the Berlaymont, the enourmoud headquarters in Brussels Belgium.  European Common Market World Headquarters in Brussels Belgium
European Common Market World Headquarters in Brussels BelgiumSanter, Jacques
"The right man in the right place at the right time," as he was called by British Prime Minister John Major, or the lowest common denominator, as others said of him, Jacques Santer came to the presidency of the European Commission as a compromise choice. He was selected for a five-year term by the European Council, the heads of government of the 12 member nations of the European Union (EU), at a special meeting on July 15, 1994, and confirmed by a majority of only 22 votes in the 567-seat European Parliament one week later. Santer was drafted after Major had vetoed the selection of Belgian Prime Minister Jean-Luc Dehaene, whose candidacy had been advanced by France and Germany. Santer, who was reelected in June 1994 to his third term as prime minister of Luxembourg, would assume the reins of the EU administration in January 1995, at a crucial time in the EU's movement toward political and economic integration. The Maastricht Treaty, which established the ground rules for that integration, was scheduled for review in 1996. Several of the "Euroskeptical" signees had begun to waver as the Commission, Parliament, and member nations battled over sharing power. Even if Santer might lack the commanding presence of his predecessor, France's Jacques Delors (for 10 years the voice of EU centralization), his skills as a quiet conciliator would still be much in demand. It was under his guidance, during Luxembourg's six-month stewardships of the rotating presidency of the European Council, that essential agreements were reached in 1985 and 1991--concerning a single economic market and the Maastricht Treaty, respectively. Santer's vision was of a federalized, "non-Napoleonic" Europe ("The more Europe is decentralized, the stronger it is," he said)--not the predominant view. Holding his own with influential Eurocrats such as the U.K.'s Sir Leon Brittan, within the Commission and outside it, would require statesmanship of the highest order.
Born on May 18, 1937, in Wasserbillig, Luxembourg, Santer graduated from the Athénée de Luxembourg, studied law at the Universities of Strasbourg and Paris (with a degree from the latter), and attended the Institute of Political Science in Paris. Shortly after beginning his law career, he entered politics, serving the Christian Social People's Party as its parliamentary secretary (1966-72; becoming Luxembourg's secretary of state for social and cultural affairs in the last year), secretary-general (1972-74), and ultimately president (1974-82). In 1975 he became a member of the European Parliament and was reelected in 1979 and 1984. He was elected Luxembourg's prime minister in 1984 and at different times during his three terms took on the additional portfolios of Finance and Communications, Treasury, and Cultural Affairs. From 1987 to 1990 he also assumed the leadership of the European People's Party, the coalition that united Christian Democratic and Christian Social parties in the European Parliament.
Jacque Delors
(b. July 20, 1925, Paris, France), French statesman who was president of the European Commission, the executive body of the European Community (EC), from 1985. The son of a courier at the Banque de France, Delors himself joined the bank in 1945, later earning a degree in economics from the Sorbonne. He became active in the Christian Trade Union Confederation (renamed the Democratic Trade Union Confederation in 1964) and was named its economic adviser in 1950. In 1962 he left the Banque de France, where he had quickly risen to an executive position, to head the social affairs division of the state's General Planning Commission. From 1969 to 1972 he served as chief adviser on social affairs to Prime Minister Jacques Chaban-Delmas's "new society" program.
Delors joined the Socialist Party in 1974 and in 1976 became the party's national delegate for international economic relations. In 1979 he was elected to the European Parliament, where he served as chairman of the economic and monetary committee. In 1981 François Mitterrand, the newly elected Socialist president, appointed Delors minister of economics and finance. The French economy was then in recession, and Delors initially carried out the Socialist recovery plan of increasing government controls and spending. He eventually convinced Mitterrand to accept his program of austerity, however, which succeeded in restoring relative economic stability.
Delors left government to become the president of the European Commission in 1985. He revitalized the long-stalled EC, pushing through reforms and persuading the member states to agree to the creation of a single market, to take effect from Jan. 1, 1993, the first step toward full economic and political integration.
EUROPE ADRIFT AFTER THE COLD WAR
For 45 years Europe had been divided by the Iron Curtain. Though tragic and often tense, the Cold War nonetheless imposed stability on Europe and allowed the western sector, at least, to prosper as never before. The end of Communism, therefore, posed several vexing questions. Would a united Germany dominate Europe economically and waver dangerously between East and West in foreign policy? Could the new democracies of east-central Europe achieve Western levels of prosperity and avoid the ethnic strife that had sparked two world wars? In the short run, the worst fears were not realized. Chancellor Kohl took every opportunity to reaffirm Germany's commitment to the idea of a united Europe, while the high cost of rehabilitating the former East Germany allayed fears of a German economic hegemony. Europe's long-term stability, however, depended on the continued vitality of institutions built up during the Cold War. Would the EC and the NATO alliance remain vigorous in the absence of a Soviet threat?In the 1980s the dynamic Jacques Delors had revived the momentum of European integration by promoting the Single European Act, under which EC members were to establish full economic and monetary union, with substantial coordination of foreign and social policies, by 1992. Most of Delors's provisions were embodied in the Maastricht Treaty approved by the 12 EC member states (Spain and Portugal had been admitted in 1986) in December 1991. This unprecedented surrender of national sovereignty worried governments and voters, however. A national referendum in France barely approved the treaty, the Danes rejected it the first time around, and the government of John Major, Thatcher's successor as British prime minister, nearly fell from power before persuading Parliament to ratify Maastricht in July 1993. The treaty went into effect on November 1. In order to create "an ever closer union among the peoples of Europe," Maastricht replaced the old EC with a new European Union (EU), enhanced the powers of the European Parliament at Strasbourg, promised monetary union by 1999, promoted common policies on crime, immigration, social welfare, and the environment, and called for "joint action" in foreign and security policy. The EU promptly voted to "broaden" as well as "deepen" its membership by approving the applications on March 29 of Norway, Sweden, Finland, and Austria (although Norwegian voters later rejected joining).
EC), formerly (until Nov. 1, 1993) EUROPEAN ECONOMIC COMMUNITY (EEC), byname COMMON MARKET, economic association of European countries that was established to promote European economic unity. The EEC was established in the wake of World War II to promote the lasting reconciliation of France and Germany, to develop the economies of the member states into one large common market, and to try to develop a political union of the states of western Europe capable of alleviating their fears of war with each other. The liberalized trade policies sponsored by the EC from the 1950s were highly successful in increasing trade and economic prosperity in western Europe. The EC is now the principal organization within the European Union (q.v.).The European Economic Community was formally established by one of the Treaties of Rome in 1957 to facilitate (1) the removal of barriers to trade among the member nations, (2) the establishment of a single commercial policy toward nonmember countries, (3) the eventual coordination of members' transportation systems, agricultural policies, and general economic policies, (4) the removal of private and public measures restricting free competition, and (5) the assurance of the mobility of labour, capital, and entrepreneurship among the members. The original members were France, Belgium, Luxembourg, The Netherlands, Italy, and West Germany. The United Kingdom, Denmark, and Ireland joined in 1973, Greece in 1981, and Portugal and Spain in 1986. The former East Germany was admitted as part of reunified Germany in 1990. Austria, Finland, and Sweden joined the European Union, and hence the EC, in 1995. (see also Index: Rome, Treaties of)
Plans for a common market in western Europe had been discussed in 1955 at a meeting in Messina, Sicily; the treaty was finally signed in March 1957, and the EEC came into operation on Jan. 1, 1958. The four primary structural organs of the EEC were the Commission, the Council of Ministers, the Court of Justice, and the European Parliament; the last two were also to serve the other two branches of the European Communities,the European Coal and Steel Community (ECSC) and the European Atomic Energy Community (Euratom). From the beginning one of the EEC's main goals was to eliminate the tariffs, customs duties, and quotas that its members imposed on each other's exports. Accordingly, the first reduction in EEC internal tariffs was implemented in January 1959, and this proved so successful in stimulating trade between member states that by July 1968 all internal tariffs had been removed. Trade among the member nations of the EEC quadrupled in value in the period from 1958 to 1968. Meanwhile, the EEC had adopted a common external tariff so that all of its member states imposed uniform duties on goods imported from nonmember nations.
A common agricultural policy was established in 1962 and consisted of a system of common guaranteed prices (expressed in dollar terms for convenience) that would offer protection against agricultural imports from lower-cost markets outside the EEC. Because of the high cost of price supports and the resentment of the manufacturing countries, which felt that they were being forced to subsidize inefficient agriculture, the community in 1979 agreed to gradually eliminate the subsidies, replacing them with an intervention price designed to prevent agricultural prices from falling below fixed levels. The European Communities came into existence on July 1, 1967, in the merger of the EEC, the ECSC, and Euratom. Previously each of these three separate organizations had its own commission (called the High Authority in the case of the ECSC) and its own council. The merger created a single Commission of the European Communities and a single Council of Ministers of the European Communities. Other executive, legislative, and judicial bodies were also collected under the umbrella of the EC. The plural was dropped from the EC's name in the 1980s as the economic integration of the nations of western Europe progressed, and the organization became known as the European Community. In 1993 the European Community became the basis for the European Union. At the same time, the European Economic Community was renamed the European Community. The economic history of the EEC (and of the EC) since the 1970s is subsumed in that of the European Union.
The New Euro Dollar Unit Now In Effect, January 1,1999
The first meeting of the European Central Bank's board will mark a new era in monetary policy and for the entire world.The new bank will be one of the most powerful economic and monetary institutions in world history, rivaling The United States Federal Reserve.On Jan. 1,1998,the European Central Bank will set interest rates of more than 290 million europeans compared to the 266 million people in the United States.Below were preposed designs for the Euro currency.


In Greek mythology, the daughter either of Phoenix or of Agenor, king of Phoenicia. The beauty of Europa inspired the love of Zeus, who approached her in the form of a white bull and carried her away from Phoenicia to Crete. There she bore Zeus three sons: King Minos of Crete, King Rhadamanthus of the Cyclades Islands, and, according to some legends, Prince Sarpedon of Lycia. She later married the king of Crete, who adopted her sons, and she was worshiped under the name of Hellotis in Crete, where the festival Hellotia was held in her honour.  The Rebirth of The Roman Empire
The Rebirth of The Roman Empire
The name and origin of Europe is unknown but mythologic tradition states the Greek God Zeus enticed a Phoenician king's daughter who was named Europa. Zeus fell in love with Europa and transformed himself into a bull. Zeus, disguised as the bull then enticed Europa onto his back where they then went to Crete. On the island of Crete, Europa became queen and the mother of Minoan kings which are said to be the earliest civilization to inhabit European soil in the time period of 3,600 BC. The creation of the city of Rome was said to be founded and created by two men named Romulus and Remus around the time period of 753 BC in which Rome was the global empire until the time period of 476 AD.

EU HISTORY OF GROWTH
http://europa.eu.int/
MARCH 2004; The European Union (EU) is a family of democratic European countries, committed to working together for peace and prosperity. It is not a State intended to replace existing states, but it is more than any other international organisation. The EU is, in fact, unique. Its Member States have set up common institutions to which they delegate some of their sovereignty so that decisions on specific matters of joint interest can be made democratically at European level. The historical roots of the European Union lie in the Second World War. The idea of European integration was conceived to prevent such killing and destruction from ever happening again. It was first proposed by the French Foreign Minister Robert Schuman in a speech on 9 May 1950. This date, the "birthday" of what is now the EU, is celebrated annually as Europe Day.
There are five EU institutions, each playing a specific role: European Parliament (elected by the peoples of the Member States); Council of the European Union (representing the governments of the Member States); European Commission (driving force and executive body); Court of Justice (ensuring compliance with the law); Court of Auditors (controlling sound and lawful management of the EU budget).
These are flanked by five other important bodies: European Economic and Social Committee (expresses the opinions of organised civil society on economic and social issues); Committee of the Regions (expresses the opinions of regional and local authorities); European Central Bank (responsible for monetary policy and managing the euro); European Ombudsman (deals with citizens' complaints about maladministration by any EU institution or body); European Investment Bank (helps achieve EU objectives by financing investment projects); A number of agencies and other bodies complete the system. The below countries are current members of The Eu or will be members in the very near future. Belgium Denmark Germany Greece Spain France Ireland Italy Luxembourg The Netherlands Austria Portugal Finland Sweden United Kingdom Czech Republic Estonia Cyprus Latvia Lithuania Hungary Malta Poland Slovenia Slovakia Bulgaria Romania Turkey. In May, 2004 Slovenia and several other countries from the old Soviet Communist block will also be granted membership into The EU.
THE EUROPE MONETARY SYSTEM
On 1 January 2002, the euro banknotes and coins were introduced in 12 Member States of the European Union, with seven different banknotes and eight coins. The euro has been a feature of the financial landscape since 1 January 1999. On 1 January 2002, it became a physical reality across Europe when the new euro banknotes and coins were introduced. The national central banks of the European Union, along with the European Central Bank, make up the European System of Central Banks (NCBs). The NCBs of Member States not participating in the current euro areas of Denmark, Sweden and the United Kingdom, have a special status which allows them to conduct their own national monetary policies, but not to take part in deciding and implementing monetary policy for the whole euro area. The Eurosystem constutes the national central banks of the euro area together with the ECB, known as the Eurosystem. The Eurosystem's primary objective is the maintenance of price stability. It meets its objectives through deciding and implementing monetary policy; conducting foreign exchange operations, and operating payment systems. The NCBs of the participating Member States played a key role in the smooth transition to the euro. Their responsibilities included, introducing the euro in their respective countries, managing the changeover from national currencies to the euro, creating the necessary systems to effectively circulate the euro banknotes and coins, withdrawing national currencies; and providing advice about and promoting the use of the euro. Links to national central bank websites; BelgiumGermanyGreeceSpainFranceIrelandItalyLuxembourgThe NetherlandsAustriaPortugalFinland
The arrival of the euro, however, means much more than exchanging one currency for another. It involves individuals and businesses not only in the countries that have joined the single currency, but all over the world. It is in Europe's best interests to familiarise themselves and the global economy with the look and feel of the euro banknotes and coins. The new coins, over 50 billion of them, have one side common to all 12 countries and a reverse side specific to each country, while the 14.5 billion banknotes look the same throughout the euro area. Altogether, the banknotes and coins produced a total new currency of over €664 billion. The current 12 Member States of the European Union now participating in the common currency are Belgium, Germany, Greece, Spain, France, Ireland, Italy, Luxembourg, The Netherlands, Austria, Portugal, and Finland. Denmark, Sweden and the United Kingdom are members of the European Union but are not as yet currently participating in the single currency. Denmark is a member of the Exchange Rate Mechanism II (ERM II), which means that the Danish krone is linked to the euro, although the exchange rate is not fixed.
THE EURO NATIONAL FLAG


This is the European flag. It is the symbol not only of the European Union but also of Europe's unity and identity in a wider sense. The circle of gold stars represents solidarity and harmony between the peoples of Europe. The number of stars has nothing to do with the number of Member States. There are twelve stars because the number twelve is traditionally the symbol of perfection, completeness and unity. The flag will therefore remain unchanged regardless of future EU enlargements. The history of the flag goes back to 1955. At that time, the European Union existed only in the form of the European Coal and Steel Community, with just six Member States. But a separate body with a larger membership, the Council of Europe, had been set up several years earlier and was busy defending human rights and promoting European culture. The Council of Europe was considering what symbol to adopt for its own use. After much discussion, the present design was adopted - a circle of twelve gold stars on a blue background. In various traditions, twelve is a symbolic number representing perfection. It is also, of course, the number of months in a year and the number of hours shown on a clock face. The circle is, among other things, a symbol of unity. So the European flag was born, representing the ideal of unity among the peoples of Europe. The Council of Europe then encouraged other European institutions to adopt the same flag and, in 1983, the European Parliament took up the call. Finally, in 1985, the flag was adopted by all EU heads of State and government as the official emblem of the European Union, which, in those days, was called the European Communities. All European institutions have been using it since the beginning of 1986.
EUROPOL 
The two law enforcement agencies named Europol and Eurojust, have been set up to help the EU member states cooperate in the fight against organized international crime. This cooperation in criminal matters is the "third pillar" of the EU. Europol and Eurojust carry out very specific tasks in the context of the dialogue, mutual assistance, joint efforts and cooperation between the police, customs, immigration services and justice departments of the EU member states. Europol became fully operational in 1999; Eurojust was set up in 2002. Both agencies are based in The Hague, The Netherlands. Europol, the European Police Office, was set up in 1992 to handle Europe wide criminal intelligence. Europol's aim is to help the EU member states cooperate more closely and effectively in preventing and combating organized international crime. Europol supports member states by making it easier for national law enforcement agencies to exchange information, providing operational analysis, including providing expertise and technical support for investigations and operations. One of Europol's duties is to establish and maintain a computerized system to allow the input, access and analysis of data. A Joint Supervisory Body, comprising two data protection experts from each EU country, monitors the content and use of all personal data held by Europol. Europol is accountable to the Justice and Home Affairs Council, the justice and home affairs ministers of all the EU countries. The Europol Management Board comprises one representative from each EU country. The EUROPOL web site
http://www.europol.eu.int/ The rule of law is fundamental to the European Union. All EU decisions and procedures are based on the Treaties, which are agreed by all the EU countries.
The Rise of The Roman Empire
JANUARY 2004; Some call it The European Common Market, The ECC, The United States of Europe, but it is the rebirth of The Roman Empire. The ECC will grow to 25 countries this year, which will include eight former Soviet bloc countries. More work still needs to be completed in the unification process. The agreement and approval of a European Constitution and the equality of a nation's voting power, regardless of it's population, are the current the main delays of The Roman Empire's rebirth.
The fall of The Roman Empire occurred around 300-500 B.C. In 800 A.D. Charlemagne, the king of Franks, briefly began the rebuilding of the empire to some degree of success, but after his death, the empire fell apart rather quickly. In 1802, Napoleon's rise to rebuild the empire also met with disaster. France's foreign minister Dominique de Villepin published a book which vindicated Napoleon's vision of a future Great European Unity of the future. In the 1930s, Hitler loyalists instituted the salute " Heil Hitler," modeled after the " Hail Caesar " tribute. Hitler envisioned a German empire of Europe. In 1933 Italy's fascist Benito Mussolini declared that The Roman Empire must rise again. Britain's 1930s leading fascists Oswald Mosely, also cried for The Empire's return. The 1946 Zurich speech of Winston Churchill included the call for a United States of Europe.
Europe has really no choice but to incorporate and consolidate it's territory, economy, and it's military into a revived Roman Empire to survive in today's globalized world economy. The only super power in the world today has been The United States, after the fall of The Soviet Union in the 1990s. The military strength of the Asian nations, mainly China, may come close to the equality and military numbers of The United States, but in economics, technology, and nuclear capabilities, The United States has had no equal in the world since 1945. One could make a point that The Roman Empire already has been reborn, and it is stronger, more aggressive, and will not hesitate to crush it's enemies when it concerns threats to it's interests, and is the richest empire ever in world history. But the capitol of today's Roman Empire isn't in Rome, Italy. It's in Washington DC . But history has proven all empires will fall, from Babylon, Egypt, Greece, Rome, and eventually, The United States. The final and last world empire will be The One World Government.
The Unitied Kingdom & Big Brother
Controversial plans to introduce a compulsory identity card scheme have been unveiled in the Queen's Speech. The cards, which had to be dropped ahead of the election, will be linked to a National Identity Register holding information on all UK residents. Home Secretary Charles Clarke said there had been "technical" changes to the new bill to take account of previous objections to the plans. Ministers say the new Identity Cards Bill will help protect people from identity fraud and theft, and tackle illegal working and immigration abuse. They claim it will disrupt the use of false and multiple identities by terrorists and other criminals, and ensure free public services are used only by those entitled to them. The ID scheme will cost an estimated £3bn and see each UK citizen being issued with a "biometric" card bearing fingerprints and other personal details which will also be stored on a new National Identity Register database. The cards will be issued by a new Home Office executive agency, which will take over the functions of the UK Passport Service and work closely with the Home Office's Immigration and Nationality Directorate. In another blow to online privacy in The United Kingdom, The House of Lords passed a law where the government may place every e-mail and phone account under surveillance with only minor amendments. The director of Privacy International, Simon Davies was quoted, " I would have no hesitation in taking legalaction against a communication service who comply with a regulation that is unlawful, illegal, dangerous. This is a another shameful episode of the government snooping on it's citizens." Below are just a few known technologies in use today or will be in use in the near future.
Global Positioning Satellites ( Used to pinpoint or monitor various areas or individuals on the planet. )
Artificial Intelligence ( A self and independent computer or program which can resolve problems as with the human brain. )
Biometrics ( The various forms of identity verification which range from scanning the eye to fingerprints. )
Facial & Voice Recognition ( Computer programs used to recognize various features and pinpoint them to an individual. )
DNA ( From a simple Q-Tip swab of a person's mouth, your DNA profile can be obtained and stored in a data base to ensure identification.or saved for future analysis. )
The British government is proposing a law that every child born should be genetically screened and their DNA recorded and then stored in a government computer data base. The proposals were welcomed by many of Britain's medical researchers claiming the data would be crucial in screening new births for the purpose of diagnosis of future health care problems. The U.K. health minister, John Reid stated, "Increasing understanding of genetics will bring more accurate diagnosis, more personalized prediction of risk, new gene based drugs and therapies which would better target treatment and prevention."The director of the Welcome Trust, which funded the UK contribution to the Human Genome Project stated, " We are delighted that the government is making efforts to turn too genetic information which is crucial to the future of the British health care system." Opponents of this new law stated these DNA records would create a future genetic underclass of civilians who may be denied jobs, health care, and even loans due to a DNA record, which future employers could use to screen out high risk applicants. US President George W. Bush has reportedly backed proposals which prohibit such " genetic branding of human beings " But in the area of politics, you tell the people what they want to hear and not the truth. Already in the US the police can take DNA samples from individuals charged with an offense, which is then stored in national data-base. An amendment to The Criminal Justice Act is already under way where anyone who is arrested, or even suspected, would be subject to having their DNA sample entered into the national data-base. In July 2000, A surveillance bill granting the U.K. government sweeping powers to access e-mail and other encrypted Internet communications passed its final vote in the House of Commons and is set to become law on Oct. 5, 2000. Among other provisions, the Regulation of Investigator Powers (RIP) bill requires Internet service providers in the U.K. to track all data traffic passing through their computers and route it to the Government Technical Assistance Center (GTAC). The GTAC is being established in the London headquarters of the U.K. security service MI5 – the equivalent to the Federal Bureau of Investigation in the U.S. The House of Commons, which had already passed the bill.
U.K. Prime Minister Tony Blair announced the approval of biometrics identify cards in October 2005 after The House of Commons passed the proposal with a 309 to 284 votes. The identity cards will store a citizen's finger prints, iris scan, and facial recognition technology. The U.K. biometrics identity cards may set the global standard for all nations in which the global population will be marked and scanned and the biometrics information then stored in a global data base.
London Hackers Quest To Stop Big Brother
The "2600" clubs are a kind of hacker "boy scout" organization and there are local 2600 chapters all around the globe. The name comes from the frequency that a dial tone emits; copying that frequency with a whistle allowed hackers in the 1970s to steal free telephone time. The London 2600 chapter, with about 100 or so members who come and go, meet once a month at the Webshack, which the hackers spell Websh@ck, accent on the last four letters, or a nearby McDonald's. Hackers often resort to hacking a corporation or government web site to get the attention of journalists, but that's not what their really about. In the minds of many 2600 members, it became clear what's on the mind of London's hackers: George Orwell. Britain's surveillance camera culture is terrifying in terms of Big Brother watching your every move. There's cameras every where. In many establishments there are five or six small cameras up on the ceiling, in plain view. And those are just the ones you can see. A multitude of stores around London have the bland black and white "C.C.T.V Camera System in Use" signs that greet shoppers as they enter the establishments. Then the elaborate network of government camera lenses that blanket all of London. They register car license plates as vehicles enter the financial district, sending off warnings if the cars don't exit after 20 minutes, designed to foil would be car bombers. They film faces of protesters who show up at any rally. In fact, police can now demand that anyone in London remove facial masks, under penalty of two year's jail time, so there's no way to foil the cameras.
Many state these elaborate surveillance systems are nothing but fiction because of the multitude of man power it would take to view and monitor all this video and audio data being gathered. We heard these kinds of paranoid scenarios when the first telephone wire taps became public. But wire taps require a police officer to be listening on the other end. Having individual officers skim through millions of hours of secret video is hardly realistic. But a man is not needed anymore to handle all these hours of gathered data. Big Brother instead uses the computer and newly developed software to do their monitoring and gathering of information. There is software such as Criminal Intelligence Visualization Software. It recognizes faces and it's smart enough to look for unusual behaviors or suspicious associations. It is in this environment, and this mindset, that London's hackers do their work. They do not analyze computer systems and learn how to break them out of spite, or some childish need to destroy: They see themselves merely accumulating knowledge that could be used in self defense if necessary. They are the citizen's militia, the Freedom Fighters of the Information Age, trying to stay one step ahead of technology that could one day be turned against them and they're worried about what might happen next. Britain and The United States and other world governments have set up the architecture for the next world dictator. Big Brother's Anti Christ.
Canada Takes DNA Database LeadJULY 2000: Canada unveiled what it said was the world's most sophisticated DNA database, capable of identifying criminals through analysis of minute amounts of blood, semen, or skin cells. The DNA Data Bank will include samples of DNA -- the unique building blocks of every living thing from young offenders as well as adults who are convicted of serious crimes. It will also include DNA taken from crime scenes. DNA databases already exist in the United States, Germany, Britain, Norway, Finland, Belgium, and Denmark. Canadian officials said the new C$10 million database, located at the Royal Canadian Mounted Police headquarters in Ottawa, was the most automated and sophisticated of its kind. " I would think that Canada stands on firm ground as being one of the forerunners in this technology and certainly we've done a great deal to improve the speed of the analysis," said Dr. Ron Fourney, who is in charge of the database. " The innovations we've developed that make it unique will be the robotics and certainly the cost effectiveness," he told a news conference at the official launch. Solicitor General Lawrence MacAuley, the minister in overall charge of Canada's law enforcement agencies, said the database was a powerful tool that would change the way in which police conducted many criminal investigations. " It will help solve serious crimes more quickly and assist in identifying repeat offenders more effectively and with more certainty. It will help police to focus their resources on key suspects by excluding the innocent more quickly," he said. The Mounties have been using DNA analysis since 1989 and the new database marks a major step forward in the fight against violent, sexual and repeat offenders, who will be required to give blood samples. The database will cost C$5 million a year to run and takes five days to process a single sample. Police estimate some 30,000 samples from known serious offenders, suspected criminals, and crime scenes will be processed a year. " When we started 10 years (ago) we might have needed a biological sample which was the size of a penny. Today's technology is so revolutionary that 10 percent of what would fit on the head of a pin is all we'd need to do a case," Fourney said. Fourney said Canada was negotiating with other nations that possess DNA databanks to set up a system whereby genetic information can be exchanged. Samples from convicted criminals will be kept permanently on file so that they can be processed again once more advanced technology becomes available. " I think the DNA Data Bank will be as revolutionary a tool for law enforcement today as fingerprinting was when it was first introduced 100 years ago," said Superintendent Lee Fraser, manager of Canada's Forensic Identification Service. " Our goal is to catch criminals and in the game of crime, knowing who the bad guys are, being able to single them out and linking them irrefutably to their crimes is a very important tool," he told the news conference.
Big Brother Takes Away Australian Citizens Registered Gun The results are in from the governments forceful taking of registered firearms from Australia's citizens in 1999. One year after gun owners were forced to surrender 640,381 personal firearms to be destroyed, including semi-automatic .22 rifles and shotguns, a program costing the government over 500 million dollars, the results are a dramatic increase in criminal activity has been experienced. Gun control advocates respond "Just wait... we'll be safer... you'll see...". Yes indeed! After 12 months of statistics the crime of homocides rose 3%, assaults rose 8%., and armed robberies increases a staggering 44% This type of governmental thinking should warn all citizens of any country to be wary of the threat of this type of Big Brother mentality. Of course, when Big Brother comes to YOUR door and not only take away your guns, but perhaps your property, your money, and even you, he doesn't want the citizens to be able to defend themselves.
Parent's Fear Big Brother's Monitoring of Their ChildrenThe mother Danielle Littflefield of Fairfax County,VA. was appalled to learn about the plans for a $11 million computer data base that would store personal information on over 150,000 school kids which would include personal and academic information, the income of a student's parents, student's report cards, behavioral problems, disabilities and disciplinary history which would begin from pre-school all the way through college. " Do we really need to be saving records of a third graders school yard fight for future employers to look at?" Mrs. Littlefield asked. Parent's have lost their fight to their children's privacy due to the 1994 congressional mandate. Over a dozen states have already begun linking through the Internet, building their sophisticated data bases on American children which is organized and ran by the US Department of Education. Fairfax County Information Superintendent John Gray was quoted as saying, " It's cheaper and more efficient for schools to collect as much information as possible and share it widely as possible." It will be just a matter of time before children will be forced to submit DNA samples which will be added to Big Brother's data base. I myself foresee DNA samples of new born children being collected at birth within the next five years.
THE TECHNOLOGY
From the Industrial Age to The Information Age
Information Technology has grown at a alarming rate in storing information with increases of 30% growth per year. In 2002 there was a estimated 5 exabytes of data. A exabyte is 5 billion gigabytes or the equivalent of 83 million computers hard drives. The Internet is now the leading source for global information and it's stability is crucial as the world has moved from the industrial age to the information age. A government's ability to gather and analyze international intelligence is paramount when establishing foreign policies. No one is immune from being watched and monitored. The coming generation of computer technology will include advanced network sensors, advanced sensors on GPS satellites, nano sensors so small they can be embedded in single piece of paper, in the lining of clothing, and any international currency. These sensors will have advanced artificial intelligence technology which will supply " early warning signals " to the Big Brother intelligence, law enforcement, and military communities. These " early warning signals " will suggest a specific event is likely to occur and provide crucial intelligence and analysis to the Big Brother communities.
THE NEW GLOBAL BAR CODE
Collaborative commerce is not just a practice between trading partners. It must be practiced between companies and their technology vendors. Thirty years ago, a group of leaders from industry and technology worked together to address a single, domestic business need. The result of that effort was the Universal Product Code which changed the world of commerce forever.
New changes will be implemented by January 01, 2005 concerning the North American Bar Code as compared to the Global Bar Code. While the rest of the world uses a 13 digit bar code, North American companies have preferred the 12 digit bar code system, but not anymore. The Uniform Code Council that oversees bar code standards in The United States and Canada announced the adoption of the 13 digit code and the code must be compliant by January 1, 2005. For the first time in history, a true global standard for bar codes will be achieved. The Bar Code itself consists of FOUR identity catagories. 1. The first set of two numbers ( 00 through 13 ) consist of the companies global origin. THE COUNTRY CODE 2. The second set of four numbers identifies the individual manufacture. THE COMPANY CODE 3. The third set of four numbers identifies the manufacturers individual product. THE ARTICLE CODE 4. The fourth set is one number that is the result of the previous 12 numbers. THE CHECK DIGIT

The Old North American Bar Code Above For More Information Visit
http://www.uccnet.org/&
http://www.uc-council.org/The Unifform Code Council
The UCC´s family of wholly-owned subsidiaries, divisions, and partnerships powerfully connects companies in the supply chain with standards-based solutions that are universally open, industry-driven, and globally endorsed. This unique position provides an unprecedented blend of integrity, value, and authority to move global business forward to a more efficient future. One of their slogans is "Six entities, speaking with one global voice" What started as a domestic, single industry mandate to administer the U.P.C. bar codes in 1971, has grown into a membership organization with a global system of commerce used by more than one million companies doing business in more than 140 countries.
THE MATRIX
The MATRIX contains 20 billion records from private databases. It is the largest database on the planet as far as the public knows. It has received $12 Million in funding from the federal government. The project is billed as a tool for state and local police, but organizers are considering giving access to the Central Intelligence Agency. In light of the recent decisions by New York and Wisconsin officials to terminate their participation in the controversial Multistate Anti-Terrorism Information Exchange, more commonly known as MATRIX, the American Civil Liberties Union of Pennsylvania today called on the General Assembly to bring Pennsylvania’s participation in MATRIX under legislative control. Alabama, Georgia, Kentucky, Louisiana, Oregon, South Carolina and Utah have also dropped out of their participation in the MATRIX, at least this is what they are saying. MATRIX is a federally funded, but controlled by a private company, Seisint, Inc. of Boca Raton, Florida. Seisint was founded in 1998 and has locations in Florida, Virginia, and London, England. Using MATRIX, governmental agents can instantaneously access information on firearms and hunting licenses, motor vehicle and driver record information, criminal history records, bankruptcy filings, professional licenses and voter registration information and numerous citizens are concerned about maintaining strict confidentiality of this information database, particularly data regarding driver’s licenses and firearm ownership. Steve Lillienthal, Policy Analyst at the Free Congress Foundation, called for states to enact laws to protect Americans from law enforcement databases. Lillienthal characterized MATRIX as a system that creates "more opportunities for misuse of your data, whether it is your credit history, drivers license information or photographs, Social Security number, business records, and whatever else they have on you in their files."
SPYWARE ON YOUR COMPUTER
If you use a computer at work, school, or even in your home, odds are you are being monitored by spyware. We have reported on this technology before, but the era of only the government of spying on you, now has your employer, teacher, children, parents, or your spouse monitoring you as well. Spyware comes in many forms. One way is in the forms of Cookies, a spy-text which is placed on your hard drive by visiting numerous web sites. These Cookies track your web surfing habits, and basically creates a computer profile of the user. Once the profile is completed, you are sent e-mails, pop-up ads, spam, and so forth, trying to sell you products which match your Internet interests. Spyware is also installed by YOURSELF without your knowledge. Numerous program downloads dubbed as freeware are far from being free. Before downloading a software program, you will see a box that states you agree to the terms of the download. If you have ever seen these terms, I doubt if most Harvard Law Professors could decipher the meaning of the terms you agree too, so most people just download the program. Within the program are various forms of spyware that are now monitoring your computer habits. With or without your knowledge, a keylogger may be installed on your computer. Once installed, this keylogger will allow unknown third parties to view your every move, which include, recording your keystrokes, chat sessions, passwords, web sites visited, e-mails sent or received, downloads, and much more. Such companies as PC Activity Monitor Pro claim their snoopware is a invisible and undetectable keylogger program for both networked and personal PCs. It captures all the users PC activity and saved to an encrypted log file. Other web sites such as http://pc-police.nethint.com/ & http://www.keyloggers.com/make the same claims, plus the monitored log file can be optionally sent via e-mail to a specified address (or saved to a specified shared resource in LAN environment) for further inspection and analysis. The information industry has seen the growth of companies specializing in the development of computer surveillance technologies.
The most common and annoying type of spyware is unscrupulously placed on your computer to track surfing habits. The other type of spyware, sometimes known as spy software, is used to monitor or record all activities occurring on the computer. Some of you might have already experienced this scenario. You get to work on Monday morning and upon turning on your computer, you realize that the settings for your homepage have been changed. No longer are you directed to your company's website but instead to some new Internet search engine with links to banks, gambling, pills, porn, and more. But a change in your homepage settings is the least of your worries. Spyware can track your surfing habits, abuse your Internet connection by sending confidential data to a third party, profile your shopping preferences and alter important system files, all of which can be done without you having any knowledge of it. There are currently hundreds and thousands of computers that become infected with spyware worldwide, everyday. This international form of cyber espionage is so recent that most people have yet to receive information about the nature of the hazards, the risks involved, or the tools necessary to combat the threat. Spyware can get into a computer as a software virus or as the result of installing a new program. Many popular programs that are distributed free on the Internet are actually comprised of some sort of spyware agent You must detect what Spyware is residing on your system as well as where it has decided to lay its ugly nest. There are currently hundreds of specialized software programs to detect its presence. Once found, all that is needed is to delete the programs. Hardware keyloggers, which are small devices about the size of an AA battery that are plugged in-line with your keyboard in order to record your keystrokes. However, consumers can easily spot a hardware keylogger. They can basically capture and transmit everything you do on your computer and relay that information to another party without your knowledge or consent.
ANALYTICAL LINGUISTICS RESEARCH
An article in the FBI Law Enforcement Bulletin titled "Statement Analysis; What Do Suspect's Words Really Reveal ? " which is credited to FBI academy instructor, Susan H. Adams, who teaches statement analysis as part of an FBI agent's interviewing and interrogation course. The FBI trains its agents to make a preliminary review of a written statement to be analyzed. All pronouns are circled, missing pronouns are noted, changes in the suspect's voice tone are underlined. The basics of this technique include the norm, which is typical verbal information indicating a truthful statement. The other is to look for any deviations from the norm, indicating a suspect's statement might be concealing the truth. Pronoun examples include, I, me, you, it. This FBI theory concludes those who are giving a statement using the pronoun "I, " which is first person singular, are being truthful, while those who omit the word "I, " may be an indication that the suspect is concealing something. Nouns are words used to name a person, place, thing, and can take on various meanings in an interview. In crimes involving family violence, the omitting of certain words or phrases may indicate a suspect's personal involvement. The balance of a suspect's statement begin with," a before," " during ," "and after", a criminal interview. The theory is the more balanced the statement, the more the statement is truthful, but any part of the statement that is lacking or incomplete, the suspect's statement is probably false. Linguistic analysis is nothing new as it was used in The Lindbergh baby kidnapping case in 1932. Errors in spelling occurred repeatedly in notes sent to the Lindberghs by the abductors, who were eventually captured. The 1970s Patricia Hearst kidnapping case by Symbionese Liberation Army ( SAL) is another example. A Dr. Miron prepared a series of reports for the FBI based on the received tape recordings from the abductors. Dr. Miron accurately described the individual who called himself " Cinque " which turned out to be Donald DeFreeze. Dr. Miron accurately predicted that Hearst would join SAL to participate in crimes, and that these individuals were suicidal and would die in a police shoot out. Other linguistic studies include psycholinguistic analysis. This method is the study of combining the speech pattern recognition with the facial expressions made during a suspect's statement. While linguistic analysis may be a helpful tool to law enforcement investigations, they are not permitted as evidence in court. The issue at hand is does linguistic analysis provide law enforcement with the " probable cause " to arrest and jail a person? Does it mean if your being questioned over the phone concerning a possible crime and your voice tone or your wording is analyzed as untruthful also constitute an arrest or making a false statement to a police officer? The answer is yes due to our current laws.
Georgia Tech has developed a new digital smelling sensor named, " surface acoustic wave" or SAW for short. SAW was initially designed to detect narcotics where a chemical is detected by measuring the disturbance it creates in sound waves traveling across the surface of a quartz crystal. The SAW sensor can also be used to detect explosive elements, biological agents, or anything that emits an odor. The SAW chip's superior accuracy overcomes other items that try to conceal illegal contraband such as coffee grounds which are often used to cover the scent of cocaine. The sensor may be used in a hand held device and is already in use at The Georgia Bureau of Investigation for drug busts. Georgia Tech's Ph. D William Hunt works with fellow researchers on SAW and claim it's smelling capabilities are far superior to any known existing computer or canine.
Biometrics & Nanotechnolgy
New advances in monitoring technology are increasing to the point that putting these type of technologies in practical and everyday use have reached the point where they are financially profitable. Such devices as the thumb optical scanner pictured above which is manufactured by Veridiacom of Sunnyvale, California uses silicon or solid state readers that rely on tiny capacitors that can sense a fingerprints topography. Such devices will be employed by all types of industries which include the military, law enforcement and financial institutions. The optical scanner uses an array of thousands of charge-cuopled devices, or CCDs, to take a digital gray-scale image of the ridges and valleys on a finger's print. Such recognition such as the scanning of a individuals finger or facial features would fall under Biometrics. Already the Bavarian Police are combining this Biometric technology with standard forms of identification which include passports to drivers license. Other technologies include Nanotechnology. A nanometer is a billionth of a meter. Nanotechnology scientists will use this science by manipulating the enzymes already located in the human body. These enzymes will perform as nano battery so certain chip implants will work at almost a 100% accuracy rate. Already the world's smallest rotary motor-enzyme nano machine called ATPase has been shown to work with a near 100% accuracy rate.
The InFoDot & RFID Tag
The InFoDot is a tracking and memory instrument designed to replace our current bar-code found on almost all items bought are sold. It's unique capabilities are it's use of a DataMatrix ECC200 and can scan images from angles whereas the bar code can not. More capabilities of InFoDot will be it's tracking and monitoring and providing information on the history of machines it's applied to. The company wwww.idplate.com has miniature the size of this monitor to the size of a small screw drivers tip. The RADIO FREQUENCY IDENTIFICATION TAG ( RFID ) is similar in nature. Microsoft along with other major manufacturers intend to install these units into computers, appliances, communication devices such as your home telephone and cell phones, and more than likely, human beings in the near future.
The evolution in computer chips and their miniature size has advanced to the point beyond human comprehension. While most citizens are aware that GPS tracking technology already exists in their cell phones and automobiles, few are aware of the tracking devices they already carry in their wallet. The latest global credit cards already have a chip implanted in the cards magnetic strip. Almost all drivers who have renewed their drivers license are unaware of the chip implant that lies in the bar code of their license. I myself found this rather disturbing and decided to try a experiment using a advanced bug detector which indicates and detects radio frequencies. I took out a credit card and a brand new American $100 bill and I scanned both items, and both were indeed were implanted with some form of a miniature type chip sensor. One might ask why any government would embed it's currency with a RFID type chip. The answer is simple. In any investigation that deals with drug lords, people who finance terrorism and other criminal activities, just follow the money. A currency embedded with a chip can be traced from the mint to the wallet or bank account of it's current holder.
In December of 2004, testing on the proposed UHF Generation 2 specifications were completed at the MET Labs Santa Clara facility ( http://www.metlab.com ). MET Labs is EPCglobal's official testing partner. Results provided proof that products could be built based on the proposed candidate specification. The EPCglobal UHF Generation 2 protocol, a consensus standard developed by more than 60 of the world's leading technology companies. This final phase testing of prototype chips, tags and readers are designed to meet the EPCglobal UHF Generation 2 specification. MET will collaborate with EPCglobal to develop a Performance Testing Specification. In addition, MET will develop and manage a program to accredit supplier and third party labs for the capability of testing and certifying tagged objects. In short, a path leading us into the 21st century where every consumer product, as well as the consumer themselves, will be tracked on a global scale.
--------- The World Economic Forum announced ObjectVideo, the leader in intelligent video surveillance software, has been selected as one of 29 Technology Pioneers for 2005. Companies selected as Technology Pioneers are developing and applying the most innovative and transformational technologies. This year's class of companies are at the forefront of cutting edge work in fields such as nanotechnology, drug development, renewable energy and wireless technology. Their work has the potential to significantly impact the way business and society operates. In line with the Forum's commitment to improving the state of the world, the Technology Pioneers program was established in 2000 to provide a new perspective on technological change. Each innovation, whether it has large or small consequences, is another step in society's attempt to harness, adapt and utilize technology to change and improve our world. The World Economic Forum is invested in monitoring and highlighting these innovations and exploring possible societal repercussions. "The World Economic Forum has long been a renowned organization that brings thought leaders together from across the globe," said Raul J. Fernandez, CEO of ObjectVideo. "We're extremely honored to be selected." --------------------------------------- The trend of electronic detection is heading toward the ability to monitor not only human beings, but food, clothing, transportation, global currency and the tracking of consumer good from the manufacturer to the warehouse, to the store, and finally to the purchaser's home. The current technology is already in use today by using such technologies as RFID tags, nano-senors with electronic beacons, veri-chips plus numerous other devices in which most use The Global Positioning Satellite ( GPS ) technology. Global entities include The United States Department of Defense, Wal-Mart, and the Gillette Company are already using this monitoring device and have incorporated it into their every day operations. One Company that is one of the leading industries in this area is EPCGlobal Inc.( www.epcglobalinc.org ) located in Lawrenceville New Jersey. EPCglobal is a joint venture between EAN International and the Uniform Code Council (UCC) created to promote the (EPC) Network as a global, multi-industry standard for supply chain identification through the use of RFID technology. The EPC network enables computers to 'see' physical objects, enabling manufacturers to track and trace items automatically throughout the supply chain. The EPC Network was developed by an academic research project headquarters at M.I.T. with labs at five additional research universities.
LINKSYS CAM & MINITATURE FLYING DRONE UAV CAM The Linksys wireless-B Internet Cam can be mounted almost anywhere and can send compressed MPEG-4 images to any computer in the world with a internet connection. The Linksys Cam has it's own self standing server, it can detect motion in a room or the area being surveyed and then e-mails these images to any e-mail of their choice. For those who want to monitor their baby sitter, their kids, or even mount one in a area across from your local police station, a suspected crooked judge or even a elected officials house whom you suspect of criminal activity, then you can play Big Brother too. And the flying cams known as a UAV or drone, have been in use for the last few years, especially by the military and law enforcement. These flying cams can be as small 15CM with a current flying capacity of 30 minutes and can download live color images of the area being surveyed. The military use these UAVs in various ways, such as sending them over a area which is engulfed by hills, trees, and other obstacles. The law enforcement and intelligent agencies also use these spies in the skies to survey and collect data over American communities whom they suspect may be infested with drug dealers, organized crime, or any citizen they suspect of criminal chicanery. And in the eyes of the government, all Americans are suspected of something they deem as unwholesome.
Big Brother Scanners

Above devices like Recognition Systems, Inc. fingerprint scanners can be used for entry into classrooms, unlocking your front door, accessing your mail, ATM machines and other convenient commodities to numerous to mention. The days spent searching for your keys, remembering passwords will go the the way of the dinosaur. The trick here is Big Brother will have a 24 hour a day monitoring system on you that will record all of your activities during the day you use these upcoming devices. Another way will be the government's school safety plan that will force students to submit their finger prints, because many schools will have these devices installed to be sure the right people are entering their school, and to check on students who are not attending or ditching school. The tracking of humans from birth to death is here and a life long record will be kept on all citizens. Former president Bill Clinton has already approved a bill that would make such electronic signatures as binding and legal as ink and pen.
Most of us hardly notice the surveillance cameras watching you at the grocery store or the bank. But lately those lenses have been looking for far more than shoplifters or the cameras perched outside surveying the parking lots for any illegal activities. Engineers at IBM's Almaden Research Center in San Jose, CA, report that a number of large retailers have implemented surveillance systems that record and interpret customer movements, using software from Almaden's BlueEyes research project. BlueEyes is developing ways for computers to anticipate users posturing by gathering video data on eye movement and facial expression. Your gaze might rest on a Web site heading, for example, and that would prompt your computer to find similar links and to call them up in a new window. But the first practical use for the research turns out to be snooping on shoppers. BlueEyes software makes sense of what the cameras see to answer key questions for retailers, including, how many shoppers ignored a promotion? How many stopped? How long did they stay? Did their faces register boredom or delight? How many reached for the item and put it in their shopping carts? BlueEyes works by tracking pupil, eyebrow and mouth movement. When monitoring pupils, the system uses a camera and two infrared light sources placed inside the product display. One light source is aligned with the camera's focus; the other is slightly off axis. When the eye looks into the camera aligned light, the pupil appears bright to the sensor, and the software registers the customer's attention. This type of software is similar to what Big Brother used at the 2001 Super Bowl, where their testing of recognition software, could scan thousands of people's faces, then compare those scanned images to known felons whose face is registered in a world wide data bank police agency such as INTERPOL or The FBI computer systems.
Beyond The Bar Code
 MIT Lab's Prototype Smart Tag
MIT Lab's Prototype Smart TagYour familiar with the bar codes that are on almost every product you buy. Those black stripes that are scanned at your friendly grocers may be replaced in the near future by a more effective method of identification branding. MIT has been developing the Smart Tag, a tiny radio frequency transmitter capable of broadcasting digital identification numbers. The smart tag would be so small it could replace the bar code on every product and be far more effective by being integrated into the Internet. The current prototype may be read from any angle plus it contains 96 bits of data. A 56 byte tag could number every grain of rice consumed on the planet. Today's radio frequency tags are used to tag livestock and manage inventory. MIT hopes to tie their smart tag via the Internet for more effective tracking and handling of tagged items. In theory these smart tags could also tag humans. Using the global satellite system ( GPS )Big Brother could easily tag humans with these tags. A individual could be traced for his movements 24 hours a day and then the data would be fed into a computer for further analysis.
BIG BROTHER EYE IN THE SKY OR SPACE STATION?

A Space Station or Big Brother's Future "Eye In The Sky"We have discussed the Global Satellite Positions (GPS) many times in our reporting. The United States "STAR WARS" defense against ICBMs launched against American soil is based on the theory of a space station or satellite that would use laser technology to blast these launched nuclear missiles in flight before they reach American soil. What I find interesting is if this program were deployed and it was successful, what what stop this same type of laser technology from blasting Global Satellite Positions from ground based facilities? Another troubling aspect is the explosion of a ICBM in the earth's atmosphere and the effects of nuclear fall out. The first employment of the STAR WARS defense element's system could be in place by 2004 beginning in Alaska as it's first deployment area. I find their is no winner in either scenario as I myself would rather be killed in a nuclear attack than live in a world as a survivor of a nuclear war. The Space Station which orbits our planet is a combined effort of several nations. This space station could easily be used much like the (GPS) in the tracking and monitoring everything to vehicles, people, livestock, and all forms of telecommunications. Former United States President Ronald Reagan's vision of STAR WARS may not be popular as to the building of some type of a missile defense system due to the fact that The Pentagon will undoubtedly use this technology for the deployment of offensive space satellite weapons. The United States is moving ahead with the Air Force's Airborne Laser program. The United States Air Force's Vision 2020 and the January 2001 Rumsfeld reports on the need of a space weapons defensive ( and offensive weapons no doubt. ) program are inevitable. Space war fare is a threatening and frightful aspect to human civilization, and will be a fact of life by the year 2015.
SATELLITES AND SECURITY BY BIG BROTHER
Above is the US Navstar Global Positioning satellite which will provide data for civilian and military applications. Before the 2003 US~IRAQ war, US Air Force director of space operations, General Franklin Blaisdell was quoted, " The United States is so dominate in space that I pity any nation who would stand up against us. " Donald Rumsfeld warned that the growing dependence on commercial and military satellites was leading us into a possible Space Pearl Harbor. The military wants intense development of space weapons which would make the United States the political and military space empire of the 21st century. Such rhetoric is normal US policy. In May 2002 FBI agent Kenneth Williams completed a series of investigations concerning the intelligence community and the report was finally released in July, 2003. The report which was released clearly showed the inability of the intelligence community such as the CIA ,NSA, and the FBI could not foresee or prevent such terrorists attacks as 911. With such revelations the US is still increasing laws such as The Patriot Act, which as we have reported previously, is nothing but a attack on the citizens of The United States and The Constitution. The reality of terror on US soil by outsiders such as the two attacks on New York City and a US citizen terrorist attack in Oklahoma City in 1995 is fueling fear throughout the US and passing new laws which invoke the privacy and rights of US citizens will continue to grow, even though these recent laws that have been passed are proven useless. Since all satellites are ran by computers, a computer super-virus could cripple the entire military, intelligence and civilian communities and their economies.
Big Brother's Trilateral Commission
The Trilateral Commission was formed in 1973 by private citizens of Japan, Europe (European Union countries), and North America (United States and Canada) to foster closer cooperation among these core democratic industrialized areas of the world with shared leadership responsibilities in the wider international system. Originally established for three years, The Trilateral Commission renewed for successive triennia (three-year periods), most recently for a triennium to be completed in 2006. When the first triennium of the Trilateral Commission was launched in 1973, the most immediate purpose was to draw together, at a time of considerable friction among governments—the highest level unofficial group possible to look together at the key common problems facing our three areas. At a deeper level, there was a sense that the United States was no longer in such a singular leadership position as it had been in earlier post-World War II years, and that a more shared form of leadership—including Europe and Japan in particular—would be needed for the international system to navigate successfully the major challenges of the coming years. First, the Trilateral Commission remains as important as ever in helping countries fulfill their shared leadership responsibilities in the wider international system and, second, its framework needs to be widened to reflect broader changes in the world. Thus, the Japan Group has become a Pacific Asian Group, and Mexican members have been added to the North American Group. The European Group continues to widen in line with the enlargement of the EU. We are also continuing in this triennium our practice of inviting a number of participants from other key areas.
The “growing interdependence” that so impressed the founders of the Trilateral Commission in the early 1970s is deepening into “globalization.” The need for shared thinking and leadership by the Trilateral countries, who (along with the principal international organizations) remain the primary anchors of the wider international system, has not diminished but, if anything, intensified. At the same time, their leadership must change to take into account the dramatic transformation of the international system. The members of the Trilateral Commission are about 350 distinguished leaders in business, media, academia, public service (excluding current national Cabinet Ministers), labor unions, and other non-governmental organizations from the three regions. The regional Chairmen, Deputy Chairmen, and Directors constitute the leadership of the Trilateral Commission, along with an Executive Committee including about 40 other members. The annual meeting of Trilateral Commission members rotates among the three regions. It was held in Washington in 2005, Warsaw in 2004, and Seoul in 2003. The 2006 plenary will be held in Tokyo. The agendas for these meetings have addressed a wide range of issues, an indication of how broadly The Commision see's the partnership among their countries. The project work of the Trilateral Commission generally involves teams of authors from our three regions working together for a year or so on draft reports which are discussed in draft form in the annual meeting and then published. The authors typically consult with many others in the course of their work. The task force reports (Triangle Papers) to the Trilateral Commission have covered a wide range of topics. The regional groups within the Trilateral Commission carry on some activities of their own. The European Group, with its secretariat based in Paris, has an annual weekend meeting each fall. The North American Group, with its secretariat based in Washington D.C. began North American regional meetings in 2002 and occasionally gathers with a special speaker for a dinner or luncheon event. The new Pacific Asian Group, with its secretariat based in Tokyo, began regional meetings in 2000. Each region carries on its own fund-raising to provide the financial support needed for the Trilateral Commission’s work.
When the Trilateral Commission was first launched, the plan was for an equal number of members from each of the three regions. The numbers soon began to grow, and ceilings were imposed about 1980. These ceilings have been raised somewhat since then as new countries came to be represented in the groups. The European group, which includes members from Austria, Belgium, the Czech Republic, Denmark, Estonia, Finland, France, Germany, Greece, Hungary, Ireland, Italy, Norway, Poland, Portugal, Republic of Cyprus, Slovenia, Spain, Sweden, the Netherlands, and the United Kingdom, now has a ceiling of 150 members. The ceiling for the North American group is 110, including 15 Canadian members, 10 Mexican members and 85 U.S. members. In 2000, the Japanese group of 85 members expanded to become a Pacific Asian group of 117 members, and includes 75 members from Japan, 11 members from Korea, 7 from Australia and New Zealand, 15 from the original five ASEAN countries (Indonesia, Malaysia, the Philippines, Singapore and Thailand). The new Pacific Asian group also includes participants from the People’s Republic of China, Hong Kong and Taiwan.
A Few Members of the Trilateral Commission
Chairmen, Deputy Chairmen and Directors North American Chairman: THOMAS S. FOLEY Partner, Akin Gump Strauss Hauer & Feld, Washington DC; former U.S. Ambassador to Japan; former Speaker of the U.S. House of Representatives
European Chairman: PETER SUTHERLAND Chairman, BP p.l.c., London; Chairman, Goldman Sachs International; former Director General, GATT/WTO, Geneva; former Member of the European Commission; former Attorney General of Ireland
Pacific Asian Chairman: YOTARO KOBAYASHI Chairman of the Board, Fuji Xerox Co., Ltd., Tokyo
North American Deputy Chairman: ALLAN E. GOTLIEB Senior Adviser, Stikeman Elliot, Toronto, ON; Chairman, Sotheby's, Canada; former Canadian Ambassador to the United States
North American Deputy Chairman: LORENZO ZAMBRANO Chairman of the Board and Chief Executive Officer, CEMEX, Monterrey, NL, Mexico
European Deputy Chairman: HERVE DE CARMOY Executive Chairman, Almatis, Frankfurt-am-Main; former Partner, Rhône Group, New York & Paris; Honorary Chairman, Banque Industrielle et Mobilière Privée, Paris; former Chief Executive, Société Générale de Belgique
European Deputy Chairman: ANDRZEJ OLECHOWSKI Leader, Civic Platform; former Chairman, Bank Handlowy; former Minister of Foreign Affairs and of Finance, Warsaw
Pacific Asian Deputy Chairman: KIM KYUNG-WON President, Institute of Social Sciences; former Ambassador to the United States and the United Nations, Seoul
Pacific Asian Deputy Chairman: SHIJURO OGATA Former Deputy Governor, Japan Development Bank; former Deputy Governor for International Relations, Bank of Japan
BIG BROTHER'S CURRENT GLOBAL INFRASTRUCTURE
The Internet The Internet has become a phenomenon in all areas of communications and information. It truly is a Computer City connected by networks and data machines on a global basis. Icann (
http://www.icann.org/ ) is the Internet Corporation For Assignning Global IP Names and Numbers and The Internet Society(
http://www.isoc.org/ ) is a non-profit, non-governmental, international, professional membership organization. Its more than 150 organization and 16,000 individual members in over 180 nations worldwide represent a veritable who's who of the Internet community
The U.S. Global Positioning System (GPS) constellation of satellites plays a major role in regional and global studies of Earth.In the face of continued growth and diversification of GPS applications, the worldwide scientific community has made an effort to promote international standards for GPS data acquisition and analysis, and to deploy and operate a common, comprehensive global tracking system.The satellites transmit signals that can be detected by anyone with a GPS receiver. Using the receiver, you can determine a individuals location with great precision. Advanced forms of GPS make location measurements to better than a centimeter. The current GPS constellation consists of 29 Block II/IIA/IIR satellites. The latest satellite was launched on March 20, 2004. Block I satellites are referred to as the original concept validation satellites developed by Rockwell International and reflect various stages of system development.
The United Nations The United Nations (
http://www.un.org ) maintains its headquarters in New York City.The United Nations (UN) became the successor to the League of Nations and absorbed much of the latter's administrative and physical apparatus when it was disbanded in 1946. International organization established by charter on Oct. 24, 1945, with the purposes of maintaining international peace and security, developing friendly relations among nations on the principle of equal rights and self determination, and encouraging international cooperation in solving international economic, social, cultural, and humanitarian problems.The term United Nations was originally used during World War II to denote those countries that were allied against the Axis powers (Germany, Japan, and Italy). A conference at Dumbarton Oaks, an estate in Washington, D.C., was the earliest attempt to permanently establish this United Nations. Representatives of the "Big Four" (United Kingdom, United States, U.S.S.R., and China) met there from Aug. 21 to Oct. 7, 1944, to draft some preliminary proposals, which were later discussed and more clearly outlined at the Yalta Conference in February 1945 by the Allied war leaders Winston Churchill, Joseph Stalin, and Franklin D. Roosevelt.
Interpol members include 181 global countries. Interpol has actively been involved for a number of years in combating Information Technology Crime. Rather than ‘re-inventing the wheel’, the Interpol General Secretariat has harnessed the expertise of its members in the field of Information Technology Crime (ITC) through the vehicle of a ‘working party’ or a group of experts. In this instance, the working party consists of the heads or experienced members of national computer crime units. These working parties have been designed to reflect regional expertise and exist in Europe, Asia, the Americas and in Africa. All working parties are in different stages of development. It should be noted that the work done by the working parties is not Interpol’s only contribution to combating ITC, but it certainly represents the most noteworthy contribution to date. Herewith is a brief outline of the achievements and the status quo of each of the working parties: Interpol exists to help create a safer world. Its aim is to provide a unique range of essential services for the law enforcement community to optimise the international effort to combat crime.Interpol is one of the world’s pre-eminent police organisation in support of all organisations, authorities and services whose mission is preventing, detecting, and suppressing crime.
Criminal Intelligence Analysis (sometimes called Crime Analysis) has been recognized by law enforcement as a useful support tool for over twenty-five years and is successfully used within the international community. Within the last decade, the role and position of Criminal Intelligence Analysis in the global law enforcement community has fundamentally changed. Whereas previously there were a few key countries acting as forerunners and promoters of the discipline, more and more countries have implemented analytical techniques within their police forces. International organisations, such as Interpol, Europol and the International Criminal Tribunal for the Former Yugoslavia (ICTY), all have Criminal Intelligence Analysts among their personnel. There are many definitions of Criminal Intelligence Analysis in use throughout the world. The one definition agreed in June 1992 by an international group of twelve European Interpol member countries and subsequently is adopted by other countries. The identification of and provision of insight into the relationship between crime data and other potentially relevant data with a view to police and judicial practice. The central task of Analysis is to help officials - law enforcers, policy makers, and decision makers - deal more effectively with uncertainty, to provide timely warning of threats, and to support operational activity by analysing crime. Criminal Intelligence Analysis is divided into operational (or tactical) and strategic analysis. The basic skills required are similar, and the difference lies in the level of detail and the type of client to whom the products are aimed. The Criminal Analysis Sub-Directorate (CAS) at Interpol currently has twelve Criminal Intelligence Analysts based in Lyon, France. The CAS staff currently comprises of eight different nationalities, enabling the unit to draw on a wide range of experience, contacts and languages. The unit currently provides three main Analytical Services; Operational Analysis, Strategic Analysis and Training / Consultancy.
The TIA
The United States is turning into a full fledged surveillance society leading the human race into a global society of Orwellian surveillance. The tremendous explosion in surveillance enabling technologies, combined with the ongoing weakening in legal restraints that protect our privacy mean that we are drifting toward a surveillance society. "Total Information Awareness" may be the closest thing to a true "Big Brother" program that has ever been seriously contemplated in the United States. TIA is based on a vision of pulling together as much information as possible about as many people as possible into a global database, making that information available to government officials, and sorting through it to try to identify terrorists or civilians whom pose a real or imagined threat to this Big Brother Society.
Federal Communications Commission
The media which covers the major areas of radio, television, and newspapers may be under government control in the near future. A incident at the 2004 Super Bowl halve time show, where two performers, Janet Jackson and Justin Timberlake, were involved in a sketch where the breast of Janet Jackson was exposed. The furor over this one incident has the FCC fining broadcasters and threatening to revoke their licensee. Incidents in 2004, include the Viacom syndicated radio show of Howard Stern, to be taken off the air waves on six channels with a fine of $495,000. Federal Regulators, prompted by Congress, are cracking down on what they deem indecent and immoral. I find this more on the lines of suppressing free speech and perhaps leading to the media being controlled by the government. If their is anything more obscene in this world, it's the controlling or editing of free speech and creative thought. I find some of the most obscene acts are committed by the government itself. Federal Communications Commission 445 12th Street SW Washington, DC 20554
The International Monetary ( IMF ) is located in Washington DC. The IMF is an organization of 184 countries, working to foster global monetary cooperation, secure financial stability, facilitate international trade, promote high employment and sustainable economic growth, and reduce poverty. The IMF is a entiy classified as the global money lender.
MI5 is the United Kingdom~Britain security intelligence agency with national intelligence priorities set by the Joint Intelligence Committee and endorsed by Ministers. MI5 is the major adviser to the British government on protective security measures. MI5 main purpose is to protect national security and economic well-being, and to support the law enforcement agencies in preventing and detecting serious crime and disseminating intelligence; investigating and assessing threats, and working with others to counter them. MI5 was created In October of 1909.
The two law enforcement agencies named Europol and Eurojust, have been set up to help the EU member states cooperate in the fight against organized international crime. This cooperation in criminal matters is the "third pillar" of the EU. Europol and Eurojust carry out very specific tasks in the context of the dialogue, mutual assistance, joint efforts and cooperation between the police, customs, immigration services and justice departments of the EU member states.
After the assassination of President William McKinley in 1901, Congress directed the Secret Service to protect the President of the United States. Protection remains the primary mission of the United States Secret Service. The Identity Theft and Assumption Deterrence Act (Public Law 105-318) amends 18 USC section 1028 to establish the offense of "Identity Theft." Penalties were established for anyone who knowingly transfers or uses, without authority, any means of identification of another person, with the intent to commit an unlawful activity that is a violation of the identity theft provisions of section 1028. The Patriot Act (Public Law 107-56) increases the Secret Service's role in investigating fraud and related activity in connections with computers. In addition it authorizes the Director of the Secret Service to establish nationwide electronic crimes taskforces to assist the law enforcement, private sector and academia in detecting and suppressing computer-based crime; increases the statutory penalties for the manufacturing, possession, dealing and passing of counterfeit U.S. or foreign obligations; and allows enforcement action to be taken to protect our financial payment systems while combating transnational financial crimes directed by terrorists or other criminals. 2002 The Department of Homeland Security is established with the passage of (Public Law 107-296) which in part, transfers the United States Secret Service from the Department of the Treasury, to the new department effective March 1, 2003.
Department of Justice To enforce the law and defend the interests of the United States according to the law; to ensure public safety against threats foreign and domestic; to provide Federal leadership in preventing and controlling crime; to seek just punishment for those guilty of unlawful behavior; to administer and enforce the Nation's immigration laws fairly and effectively; and to ensure fair and impartial administration of justice for all Americans. The Department of Justice is headed by the Attorney General of the United States. Its major component organizations include: the U.S. Attorneys (USAs) who prosecute federal offenders and represent the United States in court; the major investigative agencies as the Federal Bureau of Investigation (FBI) and the Drug Enforcement Administration (DEA) which gather intelligence, investigate crimes, and arrest criminal suspects; the Immigration and Naturalization Service (INS) which controls the border and provides services to lawful immigrants; the U.S. Marshals Service (USMS) which protects the federal judiciary, apprehends fugitives, and detains persons in federal custody; and the Bureau of Prisons (BOP) which confines convicted offenders.
As computers and access to the Internet became commonplace in homes across the United States, the FBI began to put in place measures to address crime in cyberspace. It created the Computer Investigations and Infrastructure Threat Assessment Center (CITAC) to respond to physical and cyber attacks against US infrastructure. The FBI has also played a crucial role in the investigation and prevention of computer crimes. In 1991, the FBI's Computer Analysis and Response Teams (CART) began to provide investigators with the technical expertise necessary to obtain evidence from the computers of suspects. In 1998, the FBI's National Infrastructure Protection Center (NIPC) was created to monitor the dissemination of computer viruses, worms, and other malicious programs and to warn government and business computer users of these dangers. In addition, having begun in the FBI's Baltimore Division in 1995, but branching out to most FBI field offices, the Bureau's Innocent Images Program has successfully identified and stopped large numbers of pedophiles who have used the Internet to purvey child pornography and to lure children into situations where they could be harmed. Between 1993 and 2001, the FBI's mission and resources expanded to address the increasingly international nature of crime in US localities. The FBI's budget grew by more than $1.27 billion as the Bureau hired 5,029 new Agents and more than 4,000 new Support Personnel. To prepare the FBI for both domestic and foreign lawlessness in the 21st century. At the start of the new millennium, the FBI stands dedicated to its core values and "Bright Line" ethical standards. Commitment to these values and standards ensures that the FBI effectively carries out its mission: Protect and defend the United States against terrorist and foreign intelligence threats; uphold and enforce the criminal laws of the United States; and provide leadership and criminal justice services to federal, state, municipal, and international agencies and partners.
Homeland Security Information Network to Expand Collaboration, Connectivity for States and Major Cities, February 24, 2004, The Department of Homeland Security, as part of its Homeland Security Information Network initiative, is expanding its computer-based counterterrorism communications network to all 50 states, five territories, Washington, D.C., and 50 other major urban areas to strengthen its two-way flow of threat information. This communications system will deliver real-time interactive connectivity among state and local partners and with the DHS Homeland Security Operations Center (HSOC) through the Joint Regional Information Exchange System (JRIES). Other DHS agencies participate through seats at the HSOC and their own operations centers, and the system will be further expanded within DHS operations. Each state and major urban area's Homeland Security Advisor and other points of contact will receive software licenses, technology, and training to participate in the information sharing and situational awareness that JRIES already brings to state and local homeland security personnel across the United States. Examples of other points of participation include state National Guard offices, Emergency Operations Centers, and first responder and Public Safety departments.
The Department's research and technology focus will seek to develop capabilities to detect and deter attacks on our information systems and critical infrastructures. The S&T Directorate will develop a national research and development enterprise to support homeland defense. This research and development effort will be driven by a constant examination of the nation's vulnerabilities, repeated testing of our security systems, and a thorough evaluation of the threats and weaknesses in the system. DHS will promote research and development of software and technology that will protect information systems and databases. DHS will support the telecommunications critical infrastructure by promoting research and development of tools and technology to prevent disruption or compromise of these services. This National Communication System helps maintains a close working relationship between the government and the telecommunications industry One important DHS priority will be to examine the vulnerabilities found in security systems. The emphasis will be on catastrophic terrorism - threats to the security of our homeland that could result in large-scale loss of life as well as triggering major economic repercussions. The focus will be on both evolutionary improvements to current capabilities as well as the development of revolutionary new capabilities.
DHS's Science & Technology Directorate will tap into scientific and technological capabilities in the United States to provide the means to detect and deter attacks using weapons of mass destruction. S&T will guide and organize research efforts to meet emerging and predicted needs and will work closely with universities, the private sector, and national and federal laboratories. The S&T Directorate will promote research and technology to develop sensors and systems to detect chemical and biological weapons from production to employment. The S&T Directorate will promote research and technology to develop sensors and systems which detect nuclear and radiological weapons from production to employment.
The global information explosion forced NSA to recognize it no longer had the technological advantage. The Agency had to prepare. NSA is increasing its partnerships with industry and academia and expanding its research and development, and aggressively recruiting and hiring cryptologic professionals. These changes are revolutionizing the Agency's capability to produce foreign signals intelligence and protect sensitive government communications in a digital age. These changes give warfighters and policymakers real-time insight into the adversary's mindset. These changes ensure that NSA's capabilities will continue to prevent conflict, shorten wars, and save lives. Since 1952, NSA has been the world expert on cryptology and electronic communications systems. Our early interest in cryptanalytic research and flexible storage capability led to the first large-scale and solid-state computers and the development of the tape cassette.Today, our work takes us to the worlds of knowledge discovery, advanced mathematics, quantum computing, nanotechnology, networking technologies and, of course, computer systems security.Some of the world’s toughest problems come to NSA.
NSA’s mission provides our military leaders and policy makers with intelligence to ensure our national defense and to advance U.S. global interests. This information is specifically limited to that on foreign powers, organizations or persons and international terrorists. NSA responds to requirements levied by intelligence customers, which includes all departments and levels of the United States Executive Branch. The ever-increasing volume, velocity and variety of today’s communications make the production of relevant and timely intelligence for military commanders and national policy makers more challenging than ever. The NSA has a tradition of dedicated, highly qualified people deeply committed to maintaining the nation’s security. While technology will obviously continue to be a key element of our future, NSA recognizes that technology is only as good as the people creating it and the people using it. NSA remains committed to its core mission of exploiting the Agency’s deep analytical skill and technological capabilities to ensure the nation maintains a significant strategic advantage in the advancement of U.S. interests around the world.
The Central Intelligence Agency (CIA) is an independent agency, responsible for providing national security intelligence to senior US policymakers. The Director of Central Intelligence (DCI) serves as the principal adviser to the President and the National Security Council (NSC) on all matters of foreign intelligence related to national security. Both the Director and Deputy Director of Central Intelligence are appointed by the President with the advice and consent of the Senate.
DefenseLINK is the official web site for the Department of Defense and the starting point for finding U.S. military information online. The home page for this site is located at http://www.defenselink.mil/. The mission of the Department of Defense is to provide the military forces needed to deter war and to protect the security of our country. The department's headquarters is at the Pentagon. The mission of DefenseLINK is to support the overall mission of the Department of Defense by providing official, timely and accurate information about defense policies, organizations, functions and operations. DefenseLINK first went on-line in October 1994, and is a cooperative effort between the Office of the Assistant Secretary of Defense (Public Affairs) and the Defense Technical Information Center.
The Pentagon, headquarters of the United States Department of Defense and the nerve center for command and control, is virtually a city within itself. The Pentagon presently houses approximately 23,000 military and civilian employees and about 3,000 non-defense support personnel dedicated to protecting our national interests. The Pentagon, headquarters of the Department of Defense, is one of the world's largest office buildings. The Pentagon is virtually a city in itself. Approximately 23,000 employees, both military and civilian, contribute to the planning and execution of the defense of our country.
The Peacekeeper missile is America's newest intercontinental ballistic missile. With the end of the Cold War, the US has begun to revise its strategic policy, and has agreed to eliminate the multiple re-entry vehicle Peacekeeper ICBMs by the year 2003 as part of the Strategic Arms Reduction Treaty II. Peacekeeper deactivation will occur over a 36-month period beginning in FY03 with missiles remaining on alert and fully mission capable throughout the deactivation period. The Defense Department analyzed the role of the Peacekeeper against projected threats in the post-Cold War environment and judged that its retirement would not have an adverse effect on the sufficiency of US nuclear forces. DoD plans to retain the booster stages for potential future uses such as space launch or target vehicles The Peacekeeper (designated LGM-118A) is a four-stage intercontinental ballistic missile capable of carrying up to ten independently-targetable reentry vehicles with greater accuracy than any other ballistic missile. Its design combines advanced technology in fuels, guidance, nozzle design, and motor construction with protection against the hostile nuclear environment associated with land-based systems. The Peacekeeper is a three-stage rocket ICBM system consisting of three major sections: the boost system, the post-boost vehicle system and the re-entry system. The Peacekeeper was the first U.S. ICBM to use cold launch technology. The missile was placed inside a canister and loaded into the launch facility. When launched, high-pressure steam ejected the canister from the launch silo to an altitude of 150 to 300 feet, and once the missile has cleared the silo, the first stage ignited and sent the missile on its course. This technique allowed SAC to launch the Peacekeeper from Minuteman silos despite the fact that the Peacekeeper was three times larger than the Minuteman III. An Automated Information System (AIS) can be functionally described as a combination of computer hardware and computer software, data and/or telecommunications, that performs functions such as collecting, processing, transmitting, and displaying information. Excluded are computer resources, both hardware and software, that are: physically part of, dedicated to, or essential in real time to the mission performance of weapon systems; used for weapon system specialized training, simulation, diagnostic test and maintenance, or calibration; or used for research and development of weapon systems.
As the Army Service Component Command to the U.S. Strategic Command, SMDC will see an increase in responsibilities from its current three mission areas, commanding and controlling Army space forces, integrated missile defense and computer network operations - to five mission areas. The new mission areas are global in nature and include global strike, space operations, integrated missile defense, strategic information operations, with Command, Control, Communications, Computers, Intelligence, Surveillance, and Reconnaissance (C4ISR) as the enabler.
The United States Strategic Command, or USSTRATCOM, is headquartered at Offutt Air Force Base in Nebraska. The command is one of nine U.S. unified commands under the Department of Defense.USSTRATCOM is the command and control center for U.S. strategic forces and controls military space operations, computer network operations, information operations, strategic warning and intelligence assessments as well as global strategic planning. The command is responsible for both early warning of and defense against missile attack and long-range conventional attacks. The command is charged with deterring and defending against the proliferation of weapons of mass destruction. The command has worldwide functional responsibilities not bound by any single area of operations. The command’s scope of responsibilities includes the interrelated areas of space operations, information operations, computer network operations, and strategic defense and attack. Tying these areas together is a globally focused command and control, communications and intelligence, surveillance and reconnaissance network (C3ISR).
With STRATCOM, for the first time in U. S. history, the planning, targeting and wartime employment of strategic forces came under the control of a single commander while the day-to-day training, equipping and maintenance responsibilities for its forces remained with the services, the Air Force and Navy. With over half a century of effective deterrence, the command today faces new global challenges that cross many boundaries, and require a globally oriented command, integrating space operations and global strike capabilities using the full range of weaponry available today. On Oct. 1, 2002, USSTRATCOM and U.S. Space Command both disestablished and a new U.S. Strategic Command stood up at Offutt AFB, responsible for the missions of both.
Open Source Information System ( OSIS )
The Open Source Information System (OSIS) is an unclassified confederation of systems serving the intelligence community with open source intelligence. Community Open Source Program Office (COSPO) supports all aspects of open source information systems, spanning collection, processing, analysis, and dissemination, to include network and distributed computing resources. The National Air Intelligence Center (NAIC) is the Executive Agent for a major element of OSIS, the Open Source Service Agent (OSSA). Dr. Joseph Markowitz, Director of COSPO has noted that while Allen Dulles was fond of saying that open sources provided 80% of the input to the all-source intelligence production process, "the more common contribution of open sources to the average all-source product is on the order of 20 to 30 percent." OSIS also offers specialized software and other tools to assist users in analysis and graphical interpretations of data. OSIS currently makes available the National Air Intelligence Center's (NAIC) SYSTRAN ® machine translation (MT) capability to provide "real time" rough translations of foreign language information. The MITRE Corp. has implemented a new, firewall-based architecture for OSIS. The previous architecture did not support direct connection between the internal network and the Internet, and each node required strong authentication. MITRE developed hybrid, virtual private network architecture that stresses usability and connectivity between nodes while retaining an acceptable level of security. It permits WWW between OSIS nodes providing node-to-node connectivity and Internet connectivity while reducing the need for strong authentication.
Liberal Democracy
Government in the West after World War II evolved more successfully. The democratic system was everywhere in the ascendant and brought with it greater influence for the working classes, for women, for non-European races, and for small states. The turbulent processes of open debate and decision produced an economic order that proved vastly more productive than the command economies of the East and brought greatly improved living standards for the great majority. Free elections meant that bad, or at any rate unpopular, governments were regularly dismissed by the voters with historically unparalleled ease and peacefulness. No Western democracy made war against any other.But Western democracy, however perfect its forms (and nowhere were they entirely consistent with its principles), always had problems on its hands that might in the end prove too much for it. The Soviet threat might be replaced by others, as was dramatically demonstrated in 1990 when Iraq seized the emirate of Kuwait. Class conflicts were muted rather than resolved. Nationalism still distorted voters' judgments in matters of foreign policy; greed misled them over economic policy. Demagogues abounded as much as they ever did in ancient Athens, and many politicians were corrupt.
The great experiment of European imperialism had collapsed. The two world wars robbed the powers of the will and the means to maintain overseas rule. Unfortunately, the empires were not immediately succeeded by new governmental forms fully capable of dealing with the problems of technologically backward, overpopulated, culturally premodern societies. In the Muslim world the idea of the Islamic republic arose in the 1980s. In Iran it amounted to an attempt to wed religion and government indissolubly, the religion being Shi'ite Islam. This Islamic Leninism has not yet been tried anywhere else, and in any case it cannot spread outside regions of Islamic dominance. In India a regime of more or less democratic nationalists endeavours to overcome a pervasive regionalism and social stratification that have been part of the subcontinent for most of its history. Japan has adapted to Western notions of capitalism and parliamentarism without contributing any fresh ideas. In the Third World the commonest expedient adopted was dictatorship, usually military, in which the ancient tradition of autocracy reasserted itself; but it was autocracy without its ancient stability, and of all current political forms it seems by far the least likely to deal effectively with the universal enemies: hunger, war, poverty, disease, waste, and violence. Some thinkers believe that only a form of world government can make decisive headway against these evils, but no one has yet suggested either how world government can be set up without a world war or how, if such a government did somehow come peacefully into existence, it could be organized so as to be worthy of its name. Even effective global cooperation among national governments is extremely difficult, as the story of such international bodies as already exist demonstrates all too sadly. In the circumstances it is wonderful that the one really important post-1945 innovation, the confederation of Europe, has made as much progress as it has.
Another hopeful development was the ending of the ruthless competition between the two superpowers, the former Soviet Union and the United States; but the cessation of the Cold War provoked a revival of nationalism, especially in eastern Europe. Self-determination has become the universal aspiration, and the nation-state is the universal norm; these developments, however, have not yet made for general peace. The incompatible claims of the city-states ruined ancient Greece; the modern world may yet be ruined by the claims of the nations. If man, the political animal, is to save himself and his civilizations, he cannot yet rest from seeking new forms of government to meet the ever-new needs of his times. A general, or sometimes individual, judging of the thoughts, words, and deeds of persons by God, the gods, or by the laws of cause and effect. In some religions (e.g., Christianity) the judgment is of both the living and the dead; in others (e.g., certain primitive religions in Africa) the judgment in which God rewards or punishes men according to their actions occurs only after death. The Western prophetic religions (i.e., Zoroastrianism, Judaism, Christianity, and Islam) developed concepts of the Last Judgment that are rich in imagery. Zoroastrianism, founded by the 6th-century-BC Iranian prophet Zoroaster, teaches that after death the soul waits for three nights by the grave and on the fourth day goes to the Bridge of the Requiter, where his deeds are weighed. If the good outweigh the bad, the soul is able to cross the bridge to heaven; if the bad outweigh the good deeds, the bridge becomes too narrow for the soul to cross, and it plunges into the cold and dark abyss of hell. This is not the end, however, for there will be a final overthrow of Ahriman, the prince of demons, by Ahura Mazda, the Wise Lord, who will resurrect all men, preside over a Last Judgment, and restore the world to goodness. Early Judaic writers emphasized a day of Yahweh, the God of Israel, which is also called the day of the Lord. This day, which will be a day of judgment of Israel and all nations, will inaugurate the Kingdom of God.
Christianity, further developing the concept of the Last Judgment, teaches that it will occur at the Parousia (the Second Coming, or Second Advent, of Christ in glory), when all men will stand before a judging God. In early Christian art the scene is one of Christ the judge, the resurrection of the dead, the weighing of souls, the separation of the saved and the damned, and representations of paradise and hell. Romanesque artists produced a more terrible vision of the Last Judgment: Christ is shown as a stern judge, sometimes carrying a sword and surrounded by the four mystical beasts--eagle, lion, ox, and winged man--of the apocalypse; the contrast between paradise and hell is between the awesome and the ferocious. In the gentler, more humanistic art of the Gothic period, a beautiful Christ is shown as the Redeemer, his right side undraped to reveal the wound of the lance, and both wounded hands raised high in a gesture that emphasizes his sacrifice. He is surrounded by the instruments of his Passion--cross, nails, lance, and crown of thorns. The intercessors are restored, and the scene of the Judgment is treated with optimism. In the 16th century, Michelangelo produced a radically different version of the Last Judgment in his fresco in the Sistine Chapel in Rome (1533-41): a vengeful Christ, nude like a pagan god, gestures menacingly toward the damned.
Islam likewise is rich in its imagery and conceptual expansion of the doctrine of the Last Judgment. The Day of Judgment is one of the five cardinal beliefs of Muslims. After death, persons are questioned about their faith by two angels: Munkar and Nakir. If a person has been a martyr, his soul immediately goes to paradise; others go through a type of purgatory (q.v.). At doomsday all persons will die and then be resurrected to be judged according to the records kept in two books, one containing a person's good deeds, and the other his evil deeds. According to the weight of the book that is tied around a person's neck, he will be consigned to paradise or hell. (see also Index: purgatory) In addition to the Western religions and some primitive religions, ancient Near Eastern religions had developed beliefs in a Last Judgment. In ancient Egyptian religion, for example, a dead person's heart was judged by being placed on a balance held by the god Anubis. If the heart was light, thus indicating a person's comparative goodness, the soul was allowed to go to the blessed region ruled by Osiris, god of the dead. If the heart was heavy, the soul might be destroyed by a hybrid creature called the Devouress. In the Asian religions (e.g., Hinduism, Jainism, and Buddhism) that believe in reincarnation (q.v.), the concept of a Last Judgment is not uncommon. (see also Index: samsara)
The Papacy
At the head of this church stood the papacy in Rome. Around the pope, conducting an ever-increasing volume of business, there grew up all the institutions of a centralized monarchy. The cardinals, chosen by the pope alone, formed the papal council, or the consistory. The 12th, 13th, and 14th centuries saw the rise of specialized departments to deal with legal matters, matters of penance, and finance (the Apostolic Camera); and, most important of all, it saw the rise of an elaborate chancery to direct the issue of the various forms of papal documents (known as bulls from the use of the bulla, a leaden seal used to authenticate many of them). The means of papal action beyond the immediate neighbourhood of Rome were provided by legates, either resident or specially commissioned, who enjoyed most of the sovereign authority of their master. The penalties of disobedience were excommunication (cutting off specific individuals from all human contact with the Christian community), interdict (the suspension of all the sacramental functions of the church--usually directed against an entire community or state), or, against princes, the launching of military expeditions with a papal blessing. The religious orders directly under papal protection, particularly the friars, provided a means of action and an intelligence service to set beside that provided by the collectors of papal taxes, often Italian merchants, and by the Inquisition. Founded in the early 13th century for the detection and extirpation of heresy, this institution was presided over by inquisitors drawn from the Dominican and Franciscan orders, but they answered directly to the pope and possessed an extensive staff of men outside the orders.
The Regular Clergy
Beside this hierarchy of the secular church stood the regular clergy. The earliest widespread communities of monks had been in theory strictly subordinate to their bishop. In practice, however, widespread recognition of the monastic life as the pattern of religious excellence, the active missionary work of such monks as St. Columban and St. Boniface, and the favour of great families gave the monasteries a position of substantial privilege. In the 11th century and later, such houses--led by Cluny--placed themselves directly under the protection of Rome as a means of excluding the bishop's authority; and, for the rest of the Middle Ages, quarrels over the bishop's right to secure an oath of obedience from the abbot, to visit the monastery to scrutinize its observance, and to exercise his office over the numerous churches and clergy attached to such abbeys were almost commonplace. (see also Index: monasticism, Cluny Abbey) Parallel to the growth of such conflicts was the rise of congregations of regulars, in which houses of a common observance, such as those of Citeaux, Hirsau, or Prémontré, were organized in a hierarchy that allowed the order itself to discipline and correct its members, to legislate for the whole congregation, and to ensure a common rule of life among its far-flung membership. The way of life of the friars, with their dispersed and itinerant congregations, involved a more complex organization modeled upon that provided by St. Dominic in 1216. Under Dominic's organization, the order was divided and subdivided into provinces, ruled by masters, and chapters; elaborate regulations provided for the election of masters, and legislation for the order was promulgated in assemblies of elected representatives. Most of these features were taken over by the Franciscans before the end of the 13th century. Relations with the hierarchy of the secular church were sometimes strained because the friars were under the direct protection of Rome and enjoyed a correspondingly extensive, though much contested, immunity from episcopal jurisdiction. In this way, many of the religious orders were involved in a hierarchical system of centralized dependence parallel to that of the secular church. (see also Index: Dominican)
World Level Control of Propaganda.
One of the most serious and least understood problems of social control is above the national level, at the level of the world social system. At the world level there is an extremely dangerous lack of means of restraining or counteracting propaganda that fans the flames of international, interracial, and interreligious wars. The global system consists at present of a highly chaotic mixture of democratic, semidemocratic, and authoritarian subsystems. Many of these are controlled by leaders who are ill educated, ultranationalistic, and religiously, racially, or doctrinally fanatical. At present, every national regime asserts that its national sovereignty gives it the right to conduct any propaganda it cares to, however untrue such propaganda may be and however contradictory to the requirements of the world system. The most inflammatory of such propaganda usually takes the form of statements by prominent national leaders, often sensationalized and amplified by their own international broadcasts and sensationalized and amplified still further by media in the receiving countries. The only major remedy would lie, of course, in the slow spread of education for universalist humanism. A first step toward this might be taken through the fostering of an energetic and highly enlightened press corps and educational establishment, doing all it can to provide the world's broadcasters, newspapers, and schools with factual information and illuminating editorials that could increase awareness of the world system as a whole. Informed leaders in world affairs are therefore becoming increasingly interested in the creation of world-level media and multinational bodies of reporters, researchers, editors, teachers, and other intellectuals committed to the unity of mankind.
NATIONAL POSTAL SYSTEMS;The United States.
Although the first official reference to overseas mail arrangements (concerning the receipt of overseas mail at Fairbanks' Tavern in Boston) dates to 1639, little real progress was made in building a postal system in colonial America until the appointment of Benjamin Franklin, formerly postmaster at Philadelphia, as deputy postmaster general for the American Colonies in 1753. Through diligent personal survey and inspection, he provided a more extensive, frequent, and speedier mail service, both within the Colonies and to England. Franklin built a sound foundation for the postal service in the United States, and, fittingly, he became its first postmaster general in 1775. Postal service expanded rapidly after independence: annual revenue increased from $37,935 in 1790 to $1,707,000 by 1829, when the postmaster general first became a member of the Cabinet. The heavy cost of establishing a postal structure to keep pace with the remarkable economic progress of the country and the accelerating extension of its settled area caused expenditure to rise even faster than revenue. The trend toward annual postal deficits, which began in the 1820s, often exceeded an annual figure of $5,000,000 later in the 19th century. By 1901, however, this expenditure had produced remarkable results. The accessibility, quality, and range of services provided had improved immeasurably. The number of post offices stood at a peak of 76,945. Postage rates had been considerably reduced with the gradual adoption of the principles of Rowland Hill: a single uniform rate regardless of distance was adopted in 1863 (after an interim period with two rates since 1845), and postage stamps were introduced in 1847. Free collection services came with the provision of street letter boxes in 1858. A free delivery service was established in 1863, covering 49 cities and employing 440 letter carriers. By 1900 the service was provided at 796 offices by 15,322 carriers. The rural free delivery (RFD) service was introduced in 1896 and town delivery in 1912. These delivery services have greatly expanded their scope. The vast majority of mail is delivered by carriers, about one-tenth through post-office boxes, and only a small fraction at windows or counters.
The range of services available to the public has also grown steadily since the first supplementary postal service, registered mail, was introduced in 1855. The major milestones in this progress were postal money order service (1864); international money orders (1867); special delivery (1885); parcel post, with its accessory collect on delivery (COD) and insurances services (1913); and certified mail (1955), which provides proof of posting for items without intrinsic value. In 1911 a postal savings system was inaugurated, reaching a peak of more than 4,000,000 accounts in 1947. A decline to less than 1,000,000 depositors caused the service to be discontinued in 1966. Mail was formally divided into three classes in 1863, and a fourth was added in 1879. First-class, or letter, mail (called letter post in the United Kingdom) is the basis of the postal service monopoly and, as the class of mail most commonly used by the public, has generally had a simplified rate structure. The other classes were established according to mail content: second-class consists of newspapers and magazines, third-class encompasses other printed matter and merchandise weighing less than one pound, and fourth-class mail is either merchandise or printed matter that weighs one pound or more. The addition of these classes allowed the post office to adopt more complicated rate structures that would take into account factors affecting handling costs--such as the weight of the piece and the distance it would be conveyed. Second-class mail receives preferential rates because the dissemination of information through newspapers and other publications is considered to serve the public interest.
The post office has played a vital role as a pioneer and major user of all systems of transport as each was developed: the stagecoach, steamboat, canals, and railroads; the short-lived pony express; and airlines and motor vehicles. It also helped subsidize their development. A traveling post-office system, in which mail could be sorted in transit, was introduced experimentally in 1862, and it made railway mail service the dominant form of mail conveyance well into the 20th century. The gradual reduction of passenger train services during the 1930s led to the birth of a highway post-office service in 1941. Both of these services declined rapidly in the 1950s and 1960s. Railway post-office mileage was reduced from 96,400,000 in 1965 to 10,100,000 in 1969, and the number of highway post offices in operation during that period fell from 163 to none. Conversely, annual ton-miles of airmail flown grew from 188,103,000 in 1965 to more than 1,000,000,000 by the 1980s, indicating the significant trend toward air transportation of regular mail without surcharge.
The United States maintains the largest postal system in the world, handling almost half the world's volume of postal traffic. To deal with the problem of increasing deficits and to improve the overall management and efficiency of the post office, the U.S. Congress approved the Postal Reorganization Act of 1970, signed into law Aug. 12, 1970. The act transformed the Post Office Department into a government-owned corporation, called the United States Postal Service. Congress no longer retains power to fix postal tariffs (although changes may be vetoed) or to control employees' salaries, and political patronage has been virtually eliminated. Government subsidies continued on a declining basis until 1982, after which the U.S. Postal Service itself no longer received a direct subsidy from Congress. An indirect subsidy is still paid for certain mailers, however. These mailers, primarily nonprofit organizations or small publishers, pay lower rates than others, with Congress making up the difference in cost. The corporation has authority to raise capital to modernize its equipment and buildings. It is also subject to competition from private companies, a situation that in 1977 led to the introduction of Express Mail, which guaranteed overnight delivery.
The availability of adequate funds for its mechanization and automation program has allowed the post office to benefit considerably from its sustained effort in research and development. More than half of all letter mail is handled by preparation and sorting machines, a trend greatly assisted by the ZIP (Zone Improvement Plan) Code program, which has come to be almost universally used.
ONE WORLD OR MANY
Japan has been, so far, the only non-Western country in the world to become fully industrialized. It may be significant that it began its industrialization in the 19th century, while the West was still itself industrializing and before it had built up a truly commanding lead. The same is true of Russia, the only other major case of industrialization outside western Europe and North America (taking South Africa and Australia as "European"). In the 20th century it has become increasingly clear that industrialization is not something that nations can decide to do or how to do entirely by themselves. They operate within a context of world industrialization, in a world system of states of decidedly unequal wealth and power.Throughout most of the 20th century the nations of this world system were categorized according to political or economic criteria. Applying the former resulted in the familiar "West-East" divide. This was primarily an ideological division between the developed capitalist nations, such as the United States, Germany, and Japan (counted ideologically as Western), and the developed communist or state-socialist nations, such as the countries of the former East European bloc. Attached to these were, respectively, underdeveloped capitalist nations, such as Bolivia and Bangladesh, and underdeveloped communist nations, such as China and Cuba. The West-East distinction became obsolete in the early 1990s with the collapse of the Soviet Union and of communist regimes throughout Eastern Europe.
A more significant and in many ways more interesting division arises from placing primary emphasis on the level of economic development, with political or ideological differences as subsidiary matters. This approach yields the "North-South" divide. With some anomalies--South Africa, Australia--the world is seen as divided essentially between the wealthy and powerful countries of the Northern Hemisphere and the poor, less-developed countries of the Southern Hemisphere. But the North-South dichotomy, though useful in debate, is inaccurate and misleading. A more precise economic model of the world system distinguishes among the superpowers, solely the United States at the end of the 20th century; other developed countries, such as Japan, Germany, and Britain; and the underdeveloped countries, such as China and Bolivia. We then have First, Second, and Third Worlds.
For most of the 20th century, when the U.S.S.R. was still a superpower, this model illustrated the interconnections and flow of power in the world system. It showed the global dominance of the superpowers, which, despite their usually conflicting ideological and strategic interests, shared a common interest in maintaining their world political and economic leadership. In competing with each other, the superpowers drew into their respective spheres of influence the less powerful countries of the Second and Third Worlds; but, in order to maintain the balance of power, they could in effect collude, choosing on occasion to ignore opportunities to gain at each other's expense in order to stifle political movements that sought too independent a third way.
A further refinement of the economic model looks past the level of three worlds of development to a single underlying and developing world system. Based on a historical perspective, this view, advanced especially by the American theorist Immanuel Wallerstein (b. 1930), argues that there is but a single world economy, the capitalist world economy, which has been expanding since the 17th century. This economy has, over the centuries, been expanding outward from its northwestern European base to take in an increasingly large portion of the globe. Even under the communist regimes, the Eastern European societies were seen as full participants in this system and were accordingly regarded not as aberrant socialist economies but as "collective capitalist firms." In this model, countries are classified according to their nearness to the centre of the system. There are "core countries," such as the United States and Japan; "semi-peripheral countries," such as Brazil, most eastern European states, and China; and "peripheral countries," such as Cuba and most of the poor countries of Africa and Asia. Depending on economic fortunes and fluctuations, as well as the logic of the developing system itself, countries can move in and out of these categories.
The plausibility and appeal of this model lie in its recognition of the growing internationalization of the industrial economy. Nation-states, whether capitalist or communist, are becoming increasingly subordinate to world economic developments. The politics of energy--oil, gas, nuclear power--are world politics (just as, for some considerable time, military strategy has been world strategy). Decisions about capital investment and growth are made in a world context and on a global scale. The giant multinational corporations are the most significant new actors on the world stage. They have been establishing a new international division of labour. From their point of view, it makes more sense to manufacture goods in South Korea or Taiwan, where labour is still cheap and governments compliant, than in the United States or Britain, where labour is expensive and regulation stringent. Such high-level functions as central planning and research and development can be retained in their Western homelands, where there are the necessary reserves of highly trained professional and scientific personnel. Profits can be declared in those countries where taxes are lowest. In such a way do the multinationals illustrate, even embody, the interdependence.
Agriculture and Food Supplies
The major world food developments in 1995 involved declining grain production per capita and increasing meat production. Both developments were continuations of multiyear trends. It was estimated that global grain stocks declined to record low levels in 1995, and they were expected to decline further by the end of the 1995-96 marketing year. In response, world grain prices increased sharply. The world food system continued to be affected by the two major regions that were moving in opposite directions. In China personal incomes were rising rapidly, and the population demanded more meat in its diet. In the republics of the former Soviet Union, however, incomes and meat consumption had dropped dramatically. These longer-run changes had major impacts on world food production (see Table I) and consumption in 1995. As in past years, nature and humans continued to create food emergencies in many countries--notably in Africa. The most important agricultural policy event of the year, however, may have been the creation of the World Trade Organization (WTO).The gap between world food-aid needs and food-aid deliveries from donor nations widened in 1995, and the gap was expected to grow in 1996. Global food-aid needs increased, while aid shipments from donor nations declined. Aid needs existed in Africa, Asia, the former Soviet republics, Bosnia and Herzegovina, and Latin America. Chronic food shortages and emergencies were caused by a combination of natural and man-made disasters in 1995. Conditions were made worse by higher prices for grain imports and lower grain export subsidies from the United States and the European Union (EU). The decline in food-aid shipments was caused by smaller aid budgets, mainly in the United States, and higher grain prices.
INTERNATIONAL ISSUES
Food-Aid Needs.According to a study by the Economic Research Service of the U.S. Department of Agriculture (USDA), poor countries would need about 14 million tons of food aid during the 1995-96 marketing year, an increase of 12% from the previous year. The estimate was obtained by examination of the needs of more than 60 less developed countries (LDCs). Aid needs for each country were defined as the difference between a target level of food consumption and what could be grown and commercially imported. The target was defined as the average level of food consumption per person over the previous five years. For many countries the target fell well below what would be considered minimum nutritional needs.The Food and Agriculture Organization (FAO) of the United Nations estimated that 36 million people faced severe food shortages in 1995, with more than 23 million of these people living in sub-Saharan Africa. Many more faced the insecurity of chronically scarce and uncertain food supplies. Somewhat smaller global grain supplies and higher prices added to the insecurity. With the exception of war-torn Bosnia and some countries of the former Soviet Union, most food-aid needs were in Africa, southern Asia, and Latin America. Food emergencies persisted in Africa in 1995, with drought, civil strife, and refugees adding to the chronic problems of poverty and food shortages. A severe drought hit southern Africa, and grain harvests there were down for the second consecutive year. The FAO estimated that 10 million people needed emergency assistance in the region. Mozambique, Zambia, and Zimbabwe had the greatest food-aid needs. Access to food in Angola and Mozambique was hampered by the disruptions caused by the civil strife of previous years. Civil strife also continued to disrupt food supplies elsewhere in Africa. Conflicts in Rwanda and Burundi created food emergencies at home and in the refugee camps in neighbouring Zaire and Tanzania. More than one million people in The Sudan needed food aid, primarily because of civil war. Civil war also increased food needs in Liberia and Sierra Leone. Even though Ethiopia expected an average harvest, its food-aid needs were expected to top one million tons in 1995. The country's poverty and limited potential to produce food caused its chronic food shortages.
Afghanistan and Bangladesh accounted for most of the food-aid needs in Asia. Poverty in both countries, along with the lingering effects of war in Afghanistan, created chronic food shortages. Floods in North Korea devastated crops in 1995, and by the end of the year major food shortages were arising. Most other Asian countries had experienced sustained economic growth in recent years and had been able to reduce their needs for aid by importing food through commercial channels. Food shortages were reported in Transcaucasia and Central Asia in 1995, primarily because of poor harvests, local civil strife, and the disruption of former distribution channels. Armenia, Azerbaijan, Georgia, Kyrgyzstan, Tajikistan, and the Russian republic of Chechnya all required some food aid. In general, however, the average caloric consumption in these areas was high relative to other countries with food-aid needs. Although most Latin-American countries experienced impressive economic growth in 1995, chronic food shortages persisted in Bolivia, Guatemala, Honduras, and Peru. Haiti, the poorest country in Latin America, continued to suffer from widespread poverty and poor crop production.
Food-Aid Supplies. Food-aid shipments fell by one-third in 1994-95 relative to the previous year. The United States accounted for virtually all of the drop. (See Table II.) The FAO expected a further decline in 1995-96. Shipments in 1994-95 and aid commitments for 1995-96 were the lowest since the mid-1970s and fell well below the minimum target of 10 million tons established by the World Food Conference in 1974. Not all food-aid shipments went to the poorest countries. Those countries classified as low-income food-deficit countries (with an average income below $1,345 in 1993) received 10% less food aid in 1994-95. (See Table II.) Though their needs probably would expand, they were likely to receive less aid in 1995-96.
Low Grain Stocks. In December the USDA estimated that the global supply of grain at the end of the 1995-96 marketing year (called year-end, or carryover, grain stocks) would fall to about 229 million tons--down 23% from the end of the previous year and down 37% from 1992-93. (See Table III.) The totals included wheat, rice, and coarse grains such as corn (maize), sorghum, oats, and barley. The data on year-end stocks provided an indication of the world's reserve that would be available to meet potential shortages in the following year. A carryover of 229 million tons would at first appear to be an adequate amount, since the world had never experienced a one-year shortfall of that magnitude. The figure could be misleading, however, since, because of trade barriers, grain does not flow freely between all countries. The USDA estimate of year-end stocks represented 13% of the annual world consumption, a record low. The percentage was less than that available during the world grain crisis of the early 1970s, when grain prices more than doubled and world conferences were required for addressing fears of food shortages. Global grain stocks declined steadily beginning in 1992. Most of the decline came from the major grain-exporting countries: the United States, the countries of the EU, Canada, Argentina, and Australia. Stocks in the former Soviet republics also declined sharply. The remainder of the world typically carried relatively few stocks--less than 4% of their annual consumption--and relied on grain from exporting countries to cover emergencies.
The decline in grain stocks was alarming on world markets because it was concentrated in exporting countries--especially the United States and the EU. (See Table III.) Importers such as Japan and Egypt relied on these countries for a dependable supply of grain. Stocks in exporting countries were much more effective in buffering the world grain market against shortages than were stocks in other countries. Exporters sold to the highest bidders anywhere in the world. Other countries tended to use their grain stocks only to meet domestic needs. China, for example, was expected to have nearly 30% of the world's grain stocks by the end of the 1995-96 marketing year. This development would appear surprising, since China was a major grain importer in 1995-96. China's grain stocks, however, were mainly stored in interior locations, where they were produced. Because of domestic transportation difficulties, it would typically be more difficult for coastal cities to get grain from China's interior than for them to get it from abroad. China's large stocks of grain provided food security to China's interior, but they provided little security for the rest of the world. The low levels of grain stocks in major exporting countries at the end of the 1995-96 marketing year likely would consist only of grain in the marketing channels from producers to processors and feeders. Virtually no reserve would be left to meet possible shortages the following year. In response to these conditions, grain prices on world markets increased sharply in 1995. Higher prices caused grain consumption to decline, especially grain fed to livestock.
The FAO estimated that global grain production would have to increase 4% in 1996 to provide a minimum level of food security. If the shortage experienced on grain markets during the 1970s was repeated, high prices in 1995 and beyond would be expected to encourage production and discourage consumption around the world. Grain stocks would thus be replenished in several years. World grain use in 1995 was 305 kg per person (1 kg = 2.2 lb). The amount was a drop of 2.6% from the previous year and a decline of 8% from the peak in 1986. Before 1986 grain use per person had increased, although somewhat unsteadily, for many years. The decline in per capita consumption in 1995 was partly a result of the temporary drop in grain supplies and the increase in population. The decline was also the result of longer-run dynamic changes that were taking place in world agriculture, however. Though it might first have seemed that there was some cause for concern, these changes did not necessarily imply that the world was becoming less capable of feeding its people. Rather, two forces explained most of the decline: more efficient meat production, and the restructuring of the economies of the countries of the former Soviet Union and of Eastern Europe. About 37% of the world's grain crop was fed to livestock--including cattle, hogs, poultry, sheep, horses, and goats. Although the quantity of grain fed to the world's livestock had not increased since 1986, world meat production had increased 22%. This increase was explained by an increase in the efficiency of converting grain to meat. Improved breeds and improved management explained part of the increase in feeding efficiency. Shifting to the production of poultry and pork rather than beef was also an important factor. It took about 11 kg of grain equivalent to produce one kilogram of beef, including the feed necessary to maintain the breeding herd. Approximately six kilograms of grain produced one kilogram of pork, and only three kilograms of grain were needed for one kilogram of poultry.
Since 1986 world beef production had increased little. Nearly all of the increase in meat production was due to increased pork and poultry meat. China accounted for virtually all the increase in pork production. The net result was that since 1986 the quantity of grain consumed per person in the form of meat had declined 18 kg, while meat production per person had increased between one and two kilograms. About half of the global decline in grain consumption per person since 1986 was explained by the major decline in consumption in Eastern Europe and the former Soviet Union. Over the past 10 years, grain consumed as human food had dropped 6 million tons in these countries, while grain consumed as livestock feed had dropped 64 million tons. The combined decline was equivalent to 4% of the world grain consumption. There also was a sharp decline in the production of meat and milk. Political and economic restructuring led to higher retail prices for cereals and meat and to much lower incomes. As a result, there was a small reduction in demand for grain for human food and a large reduction in meat consumption. The trends of more efficient feeding of livestock and of the shift from grain-fed beef to poultry and pork should help meet the growing world demand for meat without greatly increasing the use of grain for livestock feed. As the countries of Eastern Europe and the former Soviet Union restored economic growth, they likely would increase their demand for meat, but they also had the potential to increase their output of grain and livestock significantly.
China's meat production increased 14% in 1995, accounting for most of the growth in world production. China's meat production was up 80% above 1990 levels. Most of the increase came from hogs, which supplied more than 70% of China's meat. About half of the world's pork was produced in China. Poultry production also expanded rapidly, but from a much smaller base. The rapid expansion of meat production had a major impact on China's grain consumption. About one-fourth of the grain in China was fed to livestock. Although the production and human consumption of grain in 1995 were about the same as in 1990, consumption by livestock was up more than 50%. The additional grain came from higher imports and a reduction in year-end stocks. Between 1993 and 1995, China shifted from being a major grain exporter to being a major importer.Rapid economic growth and the associated increases in personal income were the main forces behind the expansion of meat consumption in China. The country's economy grew about 8-9% in 1995 after experiencing an extraordinarily high 50% growth over the previous four years. In addition, the annual population growth was about 14 million. In the future China could play a major role in shaping the world's supply and distribution of food. A large increase in grain production in China was not expected. If, however, rapid economic growth did continue and China's leaders permitted meat production to expand at recent rates, China--the world's leading grain producer--could quickly become the world's leading importer of grain. On the other hand, China's leaders could make a policy decision to curtail grain and meat imports. Political resistance to the growth of grain imports was evident in 1995.
In 1995 the 15 republics of the former Soviet Union continued their trend of producing and consuming much less meat. Meat production was down 10% from 1994 and down more than 50% from 1990. The decline was about equally distributed among beef, pork, sheep, and poultry. The decline in milk production slowed in 1995, but production was still 46% below 1990. The reduction in meat production in these countries greatly reduced the domestic demand for grain. In 1995 grain consumed as livestock feed was down 12% from 1994, while its use as human food was down 6%. Grain used for feed and food since 1990 was down 47% and 13%, respectively. As a result, the production and importation of grain also declined. Production in 1995 was down 8% from 1994 and 36% from 1990. Net imports (imports minus exports) of grain were only 6 million tons in 1995, compared with 42 million tons in 1990. These striking changes in livestock and grain production had a major impact on world trade and food supply-demand balances in the early 1990s. Recovery was slow from the massive disruptions to the economies of these countries following the collapse of the Soviet Union. The sharp drop in personal income and the higher prices for food forced people to reduce their consumption of meat and milk from the high levels of earlier years and switch to more bread, potatoes, and vegetables. Although the command system had collapsed, by 1995 a new infrastructure to get production inputs to farmers, to get farm produce to consumers, and to get everyone properly reimbursed had not developed. Basic questions of who owned the land also continued to block progress. Private ownership of farmland increased very slowly, with less than 5% of all agricultural land on privately owned farms by 1995.
If a Western-style agricultural sector were to develop in the republics of the former Soviet Union, farm production could greatly expand and the region could be a significant exporter of grains. Such exports could help offset the growing demand for grain in other parts of the world. After seven years of negotiations, known as the Uruguay round, member nations in 1994 agreed to significant modifications of the General Agreement on Tariffs and Trade (GATT), the set of rules governing international trade. One component of the agreement was the creation of the World Trade Organization, effective in January 1995, to oversee the implementation of the trade rules. The new rules would have major long-term implications for agricultural trade and world food security. A reliable trading system was essential for moving food efficiently from food-surplus to food-deficit countries. Most countries had erected barriers to trade of agricultural products, to protect either their farmers or their consumers. The net effect of each country's actions was an inefficient global system of agriculture, in which some countries overproduced, others underproduced, and trade was more difficult than it needed to be. Past trade agreements greatly reduced barriers to trade in manufactured products, and as a result trade flourished. Little progress was made in agriculture, however. The Uruguay round agreement, for the first time, provided a framework for halting the escalation of agricultural trade barriers and for gradually bringing them down. The long-term effect should be an improved global food system.
The basic principles of the trade rules were as follows: (1) trading should take place between countries without discrimination; (2) there should be predictable and growing access to each country's markets; (3) fair trade should be promoted; and (4) industrial countries were encouraged to assist the trade of LDCs. The main components of the GATT agreement on agriculture were the following principles. All nontariff barriers to trade were to be converted to equivalent tariffs, with all tariffs reduced an average of at least 36% over six years. Countries must allow duty-free imports of at least 3% to 5% of the domestic consumption of agricultural products. Export subsidies were to be reduced at least 36% and the volume of subsidized exports reduced at least 21% over six years. Subsidies to domestic producers of traded products would be reduced at least 20% over six years. Sanitary and phytosanitary regulations (human health standards and plant and animal safety standards) were to be based on science rather than on arbitrary rules that tended to discriminate against imports.
AGRICULTURAL COMMODITIES Grains. (For World Cereal Supply and Distribution, see Table III.) World grain consumption in 1995-96 was again expected to exceed production, further depleting year-end stocks. In December 1995 production of all grains was estimated to be down nearly 4% from the previous year. Although wheat production was up slightly from the poor harvest of 1994-95 and rice remained about the same, coarse grain production was expected to be down 9%. The decline in coarse grain production was caused by poor harvests in the United States (down one-fourth) and the former Soviet republics (down one-fifth). Grain production in 1995-96 was forecast to be higher in many of the LDCs. Because of tight supplies in the major grain-exporting countries, world grain trade in 1995-96 was forecast to continue at the level of the two previous years. A decline in coarse grain imports to Japan was expected as a result of declining livestock production and increased meat imports. China and drought-stricken Morocco were expected to increase their grain imports.
Oilseeds. (For World Production of Major Oilseeds and Products, see Table IV.) Global oilseed production in 1995-96 was forecast to decline about 2% from the record crop of 1994-95. Soybeans, which represented half of the world's oilseed crop, accounted for the decline. A record amount was forecast to be crushed in 1995-96 to produce vegetable oil and meal (a livestock feed). As a result of lower production and higher consumption in 1995-96, year-end stocks of oilseeds were forecast to decline by about 20% from the previous year. World prices of oilseeds increased throughout the last half of 1995 as supplies became tighter. The United States continued to produce about half of the world's soybeans. Its output in 1995 was estimated to be down 13% from the record harvest of 1994, as the average yield per hectare declined to a more normal level (1 ha = 2.47 ac). Soybean production was also expected to be down in China and Brazil.
Livestock and Meat. (For Livestock Inventories and Meat Production in Major Producing Countries, see Table V.) World meat production continued to expand more rapidly than population in 1995, especially in the LDCs. The FAO estimated that meat consumption per person in the LDCs would be 4% higher than in 1994, with the largest gains in East Asia and Latin America. North America and Western Europe would have small gains, and contractions would occur in the republics of the former Soviet Union, in Africa, and in the Middle East.
The continued expansion of meat production in China and reductions in the former Soviet republics affected global meat statistics in 1995. Elsewhere, Brazil expanded its cattle herd by 3.7 million head in response to growing domestic demand and farmers' expectations of higher profits. The economic crisis combined with a drought to force Mexican farmers to cut back on their cattle and hog numbers. Australia continued to switch from grass-fed to grain-fed beef to supply the expanding Asian import market. Australia also began rebuilding its sheep herd in 1995 after the devastation left by drought. Poland increased its pork production more than 10% because of ample feed supplies and increased demand. The world's livestock farmers continued to increase their efficiency throughout 1995. In major producing countries beef and veal increased 2-3%, but cattle and buffalo herds increased less than 1%. World pork production increased more than 6%, but there was virtually no increase in hog inventories.
Dairy. (For World Production of Milk, see Table VI.) Milk production in 1995 continued to decline slowly in developed countries (except in North America and Oceania) and increase in the LDCs. In the United States and Canada, the number of milk cows remained about the same, but more milk was obtained per cow. In spite of dry weather, Australia and New Zealand continued to expand their dairy herds in 1995. Their combined output was forecast to equal their record production of 1994. In the EU milk production remained about the same as in 1994. In Eastern Europe and the republics of the former Soviet Union, production continued to decline. Most of the decline in milk production in Russia occurred on former state and collective farms because of the lack of profits from commercial sales. Private farms apparently increased their production of milk, but mainly for local consumption. Throughout the LDCs increased demand, favourable weather conditions, and improved management combined to increase milk production in 1995. World prices of dairy products, including cheese, butter, and nonfat dry milk, increased substantially in the latter part of 1994 and in 1995. The increase was caused by limited export supplies by major exporters (the United States, countries of the EU, Australia, and New Zealand) and increased demand by importers.
Sugar. (For World Production of Centrifugal Sugar, see Table VII.) World sugar production in 1995-96 was forecast in November at a record 118 million tons. Production was expected to exceed consumption for the second consecutive year, allowing some rebuilding of world stocks. World sugar stocks were at record low levels at the beginning of the 1994-95 crop year. Driven by low stocks and strong demand, world sugar prices increased throughout 1994 and early 1995. Prices then declined as the prospects for a large harvest in 1995 became apparent. The strong growth in the demand for sugar continued in 1995. Growth in the population and personal income in Latin America, the Middle East, and Asia caused these areas to increase their demand for soft drinks and processed foods containing sugar. In the industrialized countries, however, there was little growth. Consumers in these countries continued to switch to alternative sweeteners such as high-fructose corn syrup and low-caloric sweeteners. Cuba's sugar production in 1995-96, forecast at four million tons, was expected to rebound from the extremely poor harvest of the previous year. The figure remained, however, well below the seven million to eight million tons harvested annually during the late 1980s and early 1990s, when Cuba's sugar industry was supported by the countries of Eastern Europe and the Soviet Union. It was thought that Cuba's export prospects may have improved when it reached a multiyear agreement in 1995 with Russia to barter sugar for oil.
Coffee. (For World Green Coffee Production, see Table VIII.) Poor weather conditions in Brazil had a major impact on world coffee production and prices in 1995-96. World production in 1995-96 was forecast to be down 8% from the previous year. Brazil's harvest was expected to be off by one-third, the lowest since 1986-87. Increased production in Mexico and Central America would only slightly offset Brazil's lowered output. Severe frosts in June and July 1994 combined with an extended dry spell to greatly reduce the 1995 yields of coffee in the major producing regions of Brazil. As a result, world coffee prices increased. The International Coffee Organization's monthly indicator price increased to $2.02 per pound in September 1994 from $1.08 in May. By mid-1995, however, prices had declined significantly.
Cocoa. (For World Cocoa Bean Production, see Table IX.) World cocoa production in 1995-96 was expected to exceed the record 1994-95 harvest by 4%. Côte d'Ivoire and Ghana, which accounted for half of the world's cocoa production, enjoyed record harvests in 1994-95 because of favourable growing conditions, improved management practices, and more trees reaching their peak performance years. The 1995-96 cocoa season, which began in October, was expected to produce another record-breaking harvest in Côte d'Ivoire.Because of drought and disease, Brazil's 1994-95 harvest was much smaller than had been forecast and the smallest in 18 years. The 1995-96 crop was expected to rebound, although not to the levels of the early 1990s. Malaysia's cocoa production was forecast to be down 7% from the previous year, a continuation of a longer-run decline. Government-owned land in Malaysia continued to be shifted from cocoa to oil-palm production. World consumption of cocoa products continued its upward trend in 1994-95 as a result of higher personal incomes in much of the world. In the United States, however, consumption had declined in recent years.
Cotton. (For World Cotton Production and Consumption, see Table X.) World cotton production in 1995-96 was forecast to be up 4% over that of 1994-95. Production was expected to exceed consumption, and for the second consecutive year the world's carryover stocks of cotton were expected to increase. Production increases were expected in countries in Africa and in Pakistan, but a smaller crop was expected in the United States. Farmers in the United States increased the area planted to cotton in 1995 by nearly 20%, but production fell short of early expectations as the yield per hectare dropped more than 20% from the relatively high 1994 yield. Cotton production in Central Asia leveled off in 1995 after several years of large declines. As was typical of many agricultural products after the collapse of the Soviet Union, the production of cotton had dropped by one-fourth between 1989 and 1994. During that same period domestic cotton consumption dropped by two-thirds. It was more profitable to export the cotton than to use it in domestic mills.
THE WORLD AT THE END OF THE 20TH CENTURYThe Bush and Clinton terms revealed how difficult it would be to design a global structure of peace based on institutions and values shared by all the Great Powers and capable of imposition upon the lesser ones. Just a few years before, foreign policy analysts had talked buoyantly of the triumph of capitalism and human rights, of the "end of history," of a new world order. By 1994, they suggested instead that the world might soon be rent by a "clash of civilizations" pitting the democracies against militant Islam and an imperial China, or by the spread of "chaos" as millions of refugees from failed societies in the southern half of the globe invaded the wealthy lands of the north, or by ecological and demographic disasters touched off by the spread of industry and disease in the Third World, or by the spread of nuclear and missile technology from pariah states and organized criminals in the former Soviet Union into the hands of terrorists. Perhaps such doomsday scenarios would prove to be exaggerated, or perhaps they would convince the leaders of the world's Great Powers how vital it was to act in concert. At the very least, the leaders of the 21st century might derive hope from the fact that humanity had survived the 20th century and take wisdom from its turbulent history.
The Quest for a New World Order
In the run-up to the Persian Gulf War, Bush had summoned the United Nations to the task of building a new world order. He was seeking to place the resistance to Iraqi aggression on a high moral plane but was also responding to critics who accused him of lacking "vision." In fact, American opinion was sharply divided on how to take advantage of the sudden, surprising victory in the Cold War. Neo-isolationists urged the United States to pare back foreign commitments, neo-nationalists wanted the country to look more to its own interests abroad, liberals hoped for a "peace dividend" that could be applied to a domestic agenda ranging from education to health care and crime, and all hoped to address the yawning deficits in the U.S. budget and trade balance. Internationalists of both parties, however, insisted that Americans would miss a historic opportunity if they turned inward after the Cold War. Twice before in the 20th century the United States had led the world to victories over tyranny only to see its plans for a democratic world order frustrated. As the only nation with the unique combination of military, economic, and ideological strengths needed to lead, the United States now had a duty to "win the peace."Was bold leadership in fact all that was needed to fashion a secure and free world order? Or must the post-Cold War international system, like all previous ones, evolve according to the play of power and interest among states? Would the end of the bipolar world eventuate in a unipolar one led by the UN? Or would it fragment into a multipolar system, with new sorts and sources of threats, such as ethnic and regional violence, terrorism, and the proliferation of weapons of mass destruction to second-level states, some of them hostile to Western values?
The Balkans
Whatever the future might hold, NATO and the EU would surely need to speak with one voice on the critical issues of the post-Cold War world. Instead, their growing disarray was nowhere so evident as in their ineffective and vacillating policies toward the former Yugoslavia. From its inception in 1918, Yugoslavia had been subject to strong centrifugal tendencies inasmuch as its many constituent ethnic groups harboured ancient and current grievances against each other. The World War II resistance leader Josip Broz Tito was able to restore Yugoslav unity but only through the imposition of Communist ideology and complicated mechanisms for doling out benefits. The balance began to teeter after Tito's death in 1980, then collapsed after January 1990, when the Yugoslav party congress voted to renounce Communism and promptly broke up in dissension. By July, Slovenians were voting for autonomy and the Serb minority in Croatia was seeking to break free to join Serbia. On December 9 Serbians elected a fiery nationalist and ex-Communist, Slobodan Milosevic, who then exploited his waning power over Yugoslav institutions to seize national assets on behalf of the Serbs. Slovenia declared independence in December. As fighting broke out over disputed territories of mixed population, the presidents of the six republics--Serbia, Croatia, Bosnia and Hercegovina, Slovenia, Macedonia, and Montenegro--failed in their efforts to revive a loose confederation. On June 25, 1991, Croatia declared independence, and the fighting spread. Thus, a multisided nationalist struggle, more in keeping with the beginning of the 20th century than its end, enflamed the Balkan Peninsula. Throughout the Cold War the United States had patronized Yugoslavia in deference to its independence from the Soviet bloc. The Bush administration, preoccupied elsewhere, defined the Yugoslav breakup as a European problem. The EC, in turn, had no desire to wade into a civil war and could not agree on a common posture until Germany abruptly recognized Slovenia and Croatia. Bosnia and Hercegovina then declared independence on December 20, followed later by Macedonia. Finally, in December 1991, the EC and United States imposed sanctions on the republics, and a UN delegation under Cyrus Vance and Sir David Owen sought Serbian support for a cease-fire and peacekeeping forces. On Feb. 21, 1992, the Security Council approved the dispatch of 14,400 UN peacekeepers (mostly British and French) to the former Yugoslavia. The Vance-Owen plan, which would have divided the provinces of Bosnia and Hercegovina and of Croatia into a crazy quilt based on local ethnic majorities, pleased no one, however, and fighting escalated throughout 1992 amid atrocities and evidence of "ethnic cleansing" (forced removal of populations) on the part of Serbs. UN sanctions, imposed on May 30, had no effect on the belligerents, while the UN peacekeeping forces had no peace to keep and no power to impose one. (see also Index: European Union, United Nations Peacekeeping Forces)
During the electoral campaign Clinton had criticized Bush for his ineffectual policy toward Bosnia and Hercegovina. After a tour of European capitals in early 1993, however, Christopher reported to him that the NATO powers were unwilling to discipline the Serbs unless the United States was willing to put its own troops on the ground. Mutual recriminations crossed the Atlantic until the very public bombing of a crowded market in Sarajevo in February 1994 forced Clinton to threaten Serbia with air strikes. At that point Russia stood up on Serbia's behalf and promoted its own plan for a partition of Bosnia. Clinton vetoed any plan that seemed to reward "Serbian aggression," yet he also refused to lift the arms embargo on the beleaguered Bosnian Muslims.
By mid-1994 the confused battle lines had somewhat clarified themselves. Slovenia was independent and at peace. Macedonia was admitted to the UN under the curious name (in deference to Greek sensibilities) The Former Yugoslav Republic of Macedonia, and a small international force, including Americans, stood guard there. Independent Croatia controlled almost all its putative territory, including the Dalmatian coast. What remained of Yugoslavia included Serbia, Montenegro, and portions of Bosnia and Hercegovina inhabited or claimed by Bosnian Serbs, including a corridor stretching almost to the Adriatic Sea. Within this noose the would-be state of Bosnia strangled, as the fighting among Serbs, Bosnian Serbs, Muslims, Muslim renegades, and Croats shifted from Sarajevo to Gorazde to Bihac. Every time the Serbs went on the offensive the UN, NATO, and United States debated whether to retaliate with air strikes, and every time a truce seemed at hand fighting broke out anew. By the autumn of 1994 the UN peacekeeping forces, far from contributing to peace, were literally being held hostage by the Serbs, who were strong enough to retaliate against UN forces for NATO air strikes or to seize their equipment should they attempt to get out. It was estimated that as many as 50,000 additional troops might be needed to extricate the UN force. Clinton pledged 25,000 American troops to such an effort, but everyone--not least the Serbs--hoped to avoid a deeper Western involvement.
For all the talk of assertive multilateralism, the fact remained that the UN, NATO, EU, and CSCE (including Russia) made no progress toward a resolution of the Balkan war between 1991 and December 1994. It was then that Carter embarked on his third mission as a freelance mediator. In the days before Christmas he shuttled between Bosnian Serbs and Muslims and fashioned an interim truce of at least four months' duration, reaffirmed in a UN-brokered accord on December 31. The truce gradually broke down during 1995, however, and few observers were hopeful of a quick ending to the bloodiest episode in European history since World War II.
The United Nations, founded in 1945 during the final phases of World War II, is the second multi-purpose international organization established in the 20th century that is worldwide in scope and membership. The first such organization was the League of Nations, established by the Treaty of Versailles in 1919. The ultimate goals of the United Nations, according to its Charter, are "to save succeeding generations from the scourge of war, . . . to reaffirm faith in fundamental human rights, . . . to establish conditions under which justice and respect for the obligations arising from treaties and other sources of international law can be maintained, and to promote social progress and better standards of life in larger freedom." Its primary purpose, therefore, is to maintain international peace and security. (see also Index: United Nations, Charter of the) Other important objectives listed in Chapter 1 of the Charter include developing friendly relations among nations based on respect for the principles of equal rights and self-determination of peoples; achieving worldwide cooperation to solve international economic, social, cultural, and humanitarian problems; respecting and promoting human rights; and serving as a centre where nations can coordinate their actions and activities toward these various ends.
SUBSIDIARY ORGANS AND SPECIALIZED AGENCIES
The United Nations network also includes special bodies, created by the General Assembly, and autonomous specialized agencies. Subsidiary organs report to the General Assembly or the Economic and Social Council or both. Some of these agencies are funded directly by the United Nations, while others are financed by voluntary contributions of governments or private citizens. In addition, the Economic and Social Council has consultative relationships with hundreds of nongovernmental organizations operating in economic, social, cultural, educational, health, and related fields.The specialized agencies also report annually to ECOSOC and often cooperate with each other and with UN organs. However, they are autonomous in that they control their own budgets and have their own boards of directors, who appoint agency heads independently of the General Assembly or secretary-general. Major specialized agencies and related organs of the United Nations include: the International Labour Organisation (ILO), Food and Agriculture Organization of the United Nations (FAO), United Nations Educational, Scientific and Cultural Organization (UNESCO), General Agreement on Tariffs and Trade (GATT), and World Health Organization (WHO). Two of the most powerful specialized agencies, yet also the most independent with respect to UN decision making, are the World Bank and the International Monetary Fund (IMF).
DEVELOPMENT OF INTERNATIONAL LAW
The United Nations, like the League of Nations, has played a major role in defining, codifying and expanding the realm of international law. The International Law Commission, established by the General Assembly in 1947, is the primary institution responsible for developing and codifying international law. The Sixth Committee of the General Assembly receives the commission's reports and debates its recommendations; it may then either convene an international conference to draw up formal conventions based on the draft or merely commend it to states. The International Court of Justice reinforces legal norms through its judgments. The commission and assembly have influenced international law in several important domains, including laws of war, law of the sea, treaty law, and human rights law.The work of the United Nations on developing and codifying laws of war has built on the previous accomplishments of the Hague Conferences, the League of Nations, and the Kellog-Briand Pact (Pact of Paris). The organization's first concern after World War II was the punishment of Nazi war criminals. As a result, the General Assembly directed the International Law Commission to formulate the principles of international law recognized at the Nürnberg trials and to prepare a draft code of offenses against the peace and security of mankind. In 1950 the commission submitted its formulation of the Nürnberg principles, which covered crimes against peace, war crimes, and crimes against humanity. The following year, the commission presented its draft articles to the General Assembly. These enumerated crimes against international law, including any act of aggression, threat of or preparation for aggression, annexation of territory, and genocide. Although the General Assembly did not adopt these reports, the commission's work in formulating the Nürnberg principles also influenced the development of human rights law.The United Nations also took up the problem of defining aggression, a task attempted unsuccessfully by the League of Nations. Both the International Law Commission and the General Assembly undertook prolonged efforts that eventually resulted in agreement in 1974. The definition of aggression, passed without dissent at that time, includes military attacks, sending armed mercenaries against another state, and allowing one's territory to be used for perpetrating an act of aggression against another state. Finally, in 1987, the General Assembly adopted a series of resolutions to strengthen legal norms in favour of the peaceful resolution of disputes and against the use of force.The United Nations has made considerable progress in developing and codifying the law of the sea as well. The International Law Commission took up the law of the sea as one of its earliest concerns, and in 1958 and 1960, respectively, the General Assembly convened the First and the Second United Nations Conferences on the Law of the Sea (UNCLOS). The First Conference approved conventions on the continental shelf, fishing, the high seas, and the territorial sea and contiguous zones; these were ratified by the mid-1960s. During the 1970s, however, the notion grew that the deep seabed should be declared the "common heritage of mankind" and should be administered by an international authority. The General Assembly called UNCLOS III in 1973 to discuss the conflicting positions on this issue, navigation, pollution, and the breadth of territorial waters. (see also Index: maritime law)The United Nations also has worked to advance the law of treaties and laws regulating relations between states. In 1989 the assembly passed a resolution declaring 1990-99 the UN Decade of International Law, to be dedicated to promoting acceptance and respect for the principles and institutions of international law. (C.M.L.)
Economic Reconstruction.
The devastation of large areas of the world and the disruption of economic relations during World War II resulted in the establishment (before the United Nations was founded) of the United Nations Relief and Rehabilitation Administration (UNRRA) in 1943. The UNRRA was succeeded by the International Refugee Organization, which operated from 1947 to 1951. To assist in dealing with regional problems, the Economic and Social Council in 1947 established the Economic Commission for Europe and the Economic Commission for Asia and the Far East. Similar commissions were established for Latin America in 1948 and for Africa in 1958.
PRINCIPLES AND MEMBERSHIP
The purposes, principles, and organization of the United Nations are outlined in the Charter. The essential principles underlying the purposes and function of the organization, listed in Article 2, include the following: the UN is based on the sovereign equality of its members; disputes are to be settled by peaceful means; members are to refrain from the threat or use of force in contravention of the purposes of the United Nations; each member must assist the organization in any action it takes under the Charter; and states that are not members of the organization are required to act in accordance with these principles insofar as is necessary to maintain international peace and security. Article 2 also stipulates a basic postulate of international law that, except to take enforcement measures, the organization shall not intervene in matters within the domestic jurisdiction of any state. New members are admitted to the United Nations on the recommendation of the Security Council and by a two-thirds vote of the General Assembly. The admittance of new members, however, has often engendered controversy. Given Cold War divisions between East and West, the requirement that the Security Council's permanent members (China, France, the Soviet Union [whose seat and membership were assumed by Russia in 1991], the United Kingdom, and the United States) concur on new members at times posed serious obstacles. By 1950 only 9 of 31 applicants had been admitted to the organization. In 1955 the 10th Assembly proposed a package deal which, after modification by the Security Council, resulted in the admission of 16 new states (4 eastern European states and 12 noncommunist states). The most contentious application for membership, however, was that of the People's Republic of China, which was placed before the General Assembly at every session from 1950 to 1971. The United States successfully opposed efforts to admit the People's Republic (Communist China) and to expel Nationalist China (Taiwan). Finally, in 1971, the United States, in an effort to improve its relationship with mainland China, refrained from blocking the assembly's vote to admit the People's Republic. As a result, Nationalist China's membership and permanent Security Council seat were given to the People's Republic. Controversy has also arisen over the issue of "divided" states, including the Federal Republic of Germany and the German Democratic Republic, North and South Korea, and North and South Vietnam. The two Germanys were admitted as members in 1973; these two seats were reduced to one with the unification in October 1990. Vietnam was admitted in 1977, after South Vietnam's defeat in 1975 and the reunification of the country. The two Koreas were granted membership in 1991.The two most significant waves of membership growth occurred as a result of decolonization and of the disintegration of the Soviet Union and the eastern European bloc. Following worldwide decolonization from 1955 to 1960, 40 new members were admitted; the General Assembly in 1960 passed a Declaration on the Granting of Independence to Colonial Countries and Peoples, which brought UN membership by the end of the 1970s to about 150 states. New states were admitted through the 1980s, with another significant increase after 1989. Many former Soviet republics were granted independent membership in the early 1990s, as were several newly constructed states in eastern Europe, bringing membership in the early 1990s to more than 175.
Economic and Social Council.
The Economic and Social Council (ECOSOC) directs and coordinates the economic, social, humanitarian, and cultural activities of the United Nations and its specialized agencies. Under the Charter, it is empowered to recommend international action on economic and social issues; promote universal respect for human rights; and work for global cooperation on health, education, cultural, and related areas. ECOSOC oversees regional commissions--for Europe, Asia, Latin America, and Africa--and six functional commissions dealing with statistics, population, social development, human rights, the status of women, and narcotics. These commissions formulate resolutions, recommendations, and international conventions on which the council and General Assembly take action. The 54 members (originally 18) of ECOSOC are elected by the General Assembly.
Arms Control and Disarmament
The founders of the United Nations hoped that the maintenance of international peace and security would lead to the control and eventual reduction of weapons. Therefore, Article 11 of the Charter empowers the General Assembly to consider principles for arms control and disarmament and to make recommendations to member states and the Security Council. Article 26 gives the Security Council the responsibility to formulate plans "for the establishment of a system for the regulation of armaments." The goal of arms control and reduction has proved elusive; nevertheless, the United Nations has facilitated the negotiation of several multilateral arms control treaties.Because of the enormous destructive power realized with the development and use of the atomic bomb during World War II, the General Assembly in 1946 created the Atomic Energy Commission to assist in the urgent consideration of the control of atomic energy and in the reduction of atomic weapons. The United States, however, promoted the Baruch Plan, which proposed the elimination of existing stockpiles of atomic bombs only after a system of international control was established and prohibited veto power in the Security Council on the commission's decisions. The Soviet Union, proposing the Gromyko Plan, wanted to ensure the destruction of stockpiles before agreeing to an international supervisory scheme and wanted to retain Security Council veto power over the commission. The conflicting positions of the two superpowers prevented agreement on international control of atomic weapons and energy.In 1947 the Security Council organized the Commission for Conventional Armaments to deal with armaments other than weapons of mass destruction, but progress in this field also was blocked by disagreement between the Soviet Union and the Western powers. As a result, in 1952 the General Assembly voted to replace both of these commissions with a new Disarmament Commission. This commission, which consisted of the members of the Security Council and Canada, was directed to prepare proposals that would regulate, limit, and balance reduction of all armed forces and armaments, eliminate all weapons of mass destruction, and ensure international control of and use of atomic energy for peaceful purposes only. In spite of vigorous efforts to achieve constructive results through the commission and through the General Assembly, little progress was made. In 1957, however, the International Atomic Energy Agency was established to promote the peaceful uses of atomic energy.The General Assembly in 1961 adopted a resolution declaring the use of nuclear or thermonuclear weapons to be contrary to international law, to the UN Charter, and to the laws of humanity. The Nuclear Weapons Test-Ban Treaty was signed on Aug. 5, 1963, by the Soviet Union, the United Kingdom, and the United States. This agreement--to which more than 100 states later adhered--prohibited nuclear tests or explosions in the atmosphere, in outer space, and underwater. In 1966 the General Assembly unanimously approved a treaty prohibiting the placement of weapons of mass destruction in Earth orbit, on the Moon, or on other celestial bodies and recognizing the use of outer space exclusively for peaceful purposes.In June 1968 the assembly approved the Treaty on the Non-Proliferation of Nuclear Weapons, which banned the spread of nuclear weapons from nuclear to nonnuclear powers; enjoined signatory nonnuclear powers not to develop or deploy nuclear weapons, in exchange for technical assistance in developing nuclear power for "peaceful purposes"; and committed the nuclear powers to engage in measures of disarmament. The treaty represents a significant commitment on the part of more than 140 signatory powers to control nuclear weapons proliferation; nevertheless, for many years the treaty, which went into effect in 1970, was not ratified by significant nuclear powers (including China and France) and many "near-nuclear" states (including Argentina, Brazil, Egypt, Israel, Pakistan, and South Africa). Some of these states signed the treaty in the early 1990s: South Africa in 1991 and France and China in 1992.The United Nations has been active in trying to eliminate other weapons of mass destruction of a variety of types and in a variety of contexts. In 1970 the General Assembly approved a treaty banning the emplacement of weapons of mass destruction on the seabed. In 1971 the assembly approved a convention (in effect in 1975) prohibiting the manufacture, stockpiling, and use of biological weapons, although many states have never acceded to it. In 1993 the Chemical Weapons Convention, prohibiting the development, production, stockpiling, and use of chemical weapons and providing for their destruction, was opened for signature.Many negotiations on disarmament have been held in Geneva. In 1962-68 negotiations were conducted by the Eighteen-Nation Committee on Disarmament; in 1969-78 by the Conference of the Committee on Disarmament; and since then by the Disarmament Commission. In 1978, 1982, and 1988 the United Nations also organized three special sessions of the General Assembly on disarmament. Although the UN General Sessions accomplished little in the way of substantive disarmament, they served to focus public attention on the issue.
History and Development
Despite the problems encountered by the League of Nations in arbitrating conflict and ensuring international peace and security prior to World War II, the major Allied powers agreed during the war to establish a new global organization to help manage international affairs in the postwar world. This agreement began to be articulated when U.S. President Franklin D. Roosevelt and British Prime Minister Winston Churchill signed the Atlantic Charter in August 1941. The name United Nations was originally used to denote the nations allied against Germany, Italy, and Japan. Twenty-six countries signed the Declaration by United Nations on Jan. 1, 1942, a document that set forth the war aims of the Allied powers.The United States, United Kingdom, and Soviet Union took the lead in designing the new organization and determining its decision-making structure and functions. Although the "Big Three" states and their respective leaders (Roosevelt, Churchill, and Joseph Stalin) eventually reached a compromise, political issues that foreshadowed the Cold War initially hindered agreement. These issues concerned membership, colonies, and voting formulas in the General Assembly and the Security Council. In the former, the Soviet Union demanded individual membership and voting rights for its constituent republics, while Britain wanted assurances that its colonies would not be put under UN control. There was also disagreement over the voting system to be adopted in the Security Council, an issue that became famous as the "veto problem." The UN Charter finally emerged as a result of three major wartime conferences--Dumbarton Oaks, Yalta, and San Francisco--that eventually resolved these problems but also provided the outlines for future political debates between East and West.The first major step toward the formulation of the United Nations was taken at the Dumbarton Oaks Conference, a meeting of the diplomatic experts of the Big Three powers plus China (a group often designated the Big Four) held Aug. 21-Oct. 7, 1944, at Dumbarton Oaks, an estate in Washington, D.C. Although the four powers agreed on the general purposes, structures, and functions of a new world organization, the conference ended amid continuing disagreement over the issues of membership and voting. At the Yalta Conference, a meeting of the Big Three in a Crimean resort city in February 1945, the powers laid the basis for charter provisions delimiting the authority of the Security Council. Moreover, Roosevelt, Churchill, and Stalin reached a tentative accord on the number of Soviet republics to be granted independent membership status. Finally, the powers agreed that the new organization would include a trusteeship system to succeed the League of Nations mandate system. (see also Index: Taiwan)
The Dumbarton Oaks proposals, with modifications from the Yalta Conference, thus formed the basis of negotiations at the United Nations Conference on International Organization (UNCIO), which convened at San Francisco on April 25, 1945, and produced the final Charter of the United Nations. At San Francisco, compromises led to the admission of the Ukrainian S.S.R. and the Belorussian S.S.R., as well as Argentina. Poland, not present at the conference, was permitted to become an original member of the UN. In addition, Security Council veto power (among the permanent members) was affirmed, although any member of the General Assembly could raise issues for discussion. Other political issues that were resolved by compromise concerned the line between domestic jurisdiction versus international competence for the protection of human rights and the promotion of economic and social welfare; the status of colonial areas and the distribution of trusteeships; the status of regional and defense arrangements; and Great Power dominance versus the equality of states.
Representatives of 50 nations attended the San Francisco Conference. Nine continental European states, 21 American republics, 7 Middle Eastern states, 5 Commonwealth nations, 2 Soviet republics (in addition to the U.S.S.R. itself), 2 East Asian nations, and 3 African states represented all geographic areas of the world. The United Nations Charter was unanimously adopted and signed on June 26 and entered into force on Oct. 24, 1945.
The World Health Organization
The World Health Organization has included nursing in its activities from its beginning in 1948. Nurses are included on teams such as those concerned with maternal and child health, malaria, and tuberculosis. Member nations request assistance in developing educational programs for nurses, auxiliaries, and midwives and to organize public health programs and hospitals. Countries are assisted in establishing nursing as a part of their national health departments to assure the planning and implementing of the nursing portions of programs. Governments are aided in the establishment of nursing and nursing-education systems, including those in midwifery. Other programs in which assistance is given include upgrading diploma schools; development of basic and post-basic programs in universities; revision of entry requirements; coordination of classroom teaching with the clinical practice of students; adaptation of hospitals and health agencies for students' experience; preparation of public health nurses, administrators, midwives, and teachers, including teachers of auxiliaries and of indigenous midwives. (In many countries more than half of all the births are attended by untrained midwives.)
Fellowships are granted to nurses for overseas study, mostly in the areas of teaching, administration, public health nursing, midwifery, maternal and child health, and for learning to plan health services. When consultants from the World Health Organization work in countries, they strive to leave national counterpart personnel to continue the work. Study outside the country may be needed to develop such personnel.
THE DATA BROKER IS THE PERFECT SYMBOLIC FORM FOR BIG BROTHER
2005 JUNE: The Dutch publishing icon, Reed Elsevier, whom acquired the Florida based data-broker company Seinst last year was eager to to exploit the lucrative role that Seinst was playing in helping law enforcement agencies across the United States in tracking down all sorts of alleged unsavory individuals from terrorists, child predators, and fathers who missed child support payments. The Reed Elsevier proved it's financial savvy when it bought Seinst when it reported a 20% increase in profits in it's risk management division. Seinst's data-base was capable of processing billions of public records in seconds to identify and find people. The $775 million dollars which Reed Elsevier had reportedly paid to buy Seinst in 2004 was a Big Brother dream and a nightmare to the public and the citizen's of the United States. The Seinst massive computer network data-base was a perfect tool for the credit and insurance industries. Within a nano-second companies could acquire virtually all information on companies as well as individuals to evaluate the risk factor in granting loans, credit, or insurance to prospective customers as well as identity verification.
The selling of individual information has quietly grown into a unregulated industry, known as data-brokers. They have spent millions of dollars lobbying in Washington and stuffing money into the pockets of political campaigns in hope of going on as they have for years, unchecked and unregulated. Numerous political analysis feel the data-broker industry will soon be subject to federal rules that will govern their activity and behavior which in itself, is almost as frightening as the data-brokers going unchecked. It would be the combination of government and corporate entities that deal in the access and the selling of every American citizen's information and no doubt would be escalated to a global scale. And the abuses of this globsl data-broker computer are just now being uncovered. The Reed Elsevier web sites include
http://www.reed-elsevier.com/ &
http://www.reedbusiness.com/Reed Elsevier announced a binding offer to acquire MediMedia’s European and US Netter professional medical publishing businesses and has made a binding offer to acquire MediMedia's European and US Netter professional medical publishing businesses (MediMedia MAP) for €270 million in cash. Reed Business Information is North America's largest business-to-business information provider, covering 23 market sectors with more than 100 market leading publications and 75 Websites, as well as a range of numerous other services.
In April of 2005, Reed Elsevier stated that unauthorized individuals were using the passwords of Seinst customers and had gained access to the personal information of over 300,000 people. Another data-broker, ChoicePoint announced in February of 2005 that the consumer data of 145,000 had been stolen from it's data base. On the ChoicePoint web site they had posted the message; ChoicePoint sincerely apologizes to consumers whose information may have been accessed by criminals in the customer fraud incident. As a result of these experiences, we have taken a number of actions. ChoicePoint is headquartered outside of Atlanta GA in the United States. On the ChoicePoint web site it claims their function was the nation's premier source of data to the insurance industry into the premier provider of decision making intelligence to businesses and government. Through the identification, retrieval, storage, analysis and delivery of data, ChoicePoint serves the informational needs of businesses of all sizes, as well as federal, state and local government agencies and has also appointed Robert McConnell, a 28 year veteran of the Secret Service and former chief of the federal governments Nigerian Organized Crime Task Force, to serve as ChoicePoint's liaison to law enforcement officials. ChoicePoint's web sites include
http://www.choicepoint.com/ &
https://www.choicepointonline.com/Data-Brokers use various methods to accumulate information.. The most common forms include retrieving information from The Department of Motor Vehicles which issues drivers licenses and documents filed in courts. One newspaper investigative reporter obtained a report of a person in the Seisint's data-base and the information in the report is staggering. The report included the person's social security number, political affiliations, date of birth, every address the person had lived at, vehicles registered, the name's and birth dates of the person's family as well as the person's neighbors and their phone numbers, the average age of the neighborhood's inhabitants, education history and schools attended, the household income and the real estate value of the home, criminal records and arrests, ownership of a hunting or fishing license, permits, permits on carrying a gun, DNA and fingerprint information. All of this on one person's report! Data-Brokers claim their business activities are justified in the collecting and the selling of a individual's information to legitimate businesses that include credit and identity verification. To exploit and sell a human being's life history for money is not justified no matter what the data-brokers claim. If a person's credit card number is stolen, it constitutes a inconvenience and annoyance by the individual. But when a person's identity is stolen in such scenarios as someone using a person's identification to obtain a loan, or someone is using that person's identity to commit crimes and other criminal acts, the victim is faced with an almost impossible task in clearing their name or restoring their credit. As of May 2005, over 5 million people have had their identity stolen already. One of the major reasons is that these data-broker companies fail to encrypt the data-base's information and protect their information in a sloppy and negligent manor.
BIG BROTHER IN THE USA AND EUROPE GROWS
JULY 2004; The EU Transport Commissioner Loyola de Palacio and U.S. Secretary of State Colin Powell signed the agreement which will combine The American GPS and the European system named Galileo. The merger further advance the global monitoring satellite program. World users will, with a single receiver, be able to use either of the systems or both of the systems at the same time, promising coverage that is more, precise and continuous. The Pentagon, which controls GPS, initially attacked Galileo as unnecessary and a potential security threat during wartime, saying Galileo signals could interfere with the next generation GPS signals intended for use by the U.S. military. The United States is spending $875 million to upgrade it's GPS with a stronger military signal that will be less vulnerable to enemy interference than the weaker civilian signal currently in use. The upgrade should be completed in the next decade. The 3.6 billion euro ($4.3 billion) Galileo project is slated to go online in 2008. Its 27 satellites would more than double the coverage provided by GPS. For Europe, the satellite deal also lays the groundwork for separate, pay services that can be used in applications requiring a higher degree of accuracy in GPS's civilian monitoring and surveillance. In addition, European officials also envisage a more advance service for government agencies, such as intelligence services, the military, and police forces.
US MAINTAINS CONTROL OF THE INTERNET
2005 DEC. 23: The British news paper The London Independent recently printed a story of the US control of the Internet: "We've all gotten used to the US acting unilaterally and ignoring world opinion, but when it comes to whom controls the most vital communication tool which the world depends on, we were hoping the Americans would share." At the World Summit meeting in Tunisia the US will let the California based nonprofit Internet Corporation for Assigned Names and Numbers ( ICANN ) continue to be in control of assigning domain names and IP numbers. Every country whom attended the summit wants the ICANN Internet control handed over to The United Nations. The European Union went to the summit united with China, India, and Brazil who all argued against the US control of the Internet but the US refused to cede ground. The US argued that a United Nations control of the Internet would lead to censorship. Edinburgh's The Scotsman reported at the summit the countries who were screaming the loudest were totalitarian hellholes like Zimbabwe and Iran. The Paris newspaper Le Monde ran an article that ICANN, in theory, could disable all of France's domain names, which end with .fr. Berlin reporter Matthias Spielkamp who writes for Die Tageszeitung, made a interesting observation by writing," Corporations who dominate Internet can be a danger in themselves. Just look at what Google and Yahoo have done to gain the Chinese market. Google agreed to the Chinese government to filter out any political content that the Chinese government feels is inappropriate. The one thing that effects our lives concerning the world's largest communication system should not be controlled." In fact, 51 of 100 of the largest global economic entities are Corporations and not Nations. China and India are rapidly growing in the global world supply chain. India itself has become the current leading provider of technical services. A powerful tool is only safe when used properly and the Internet is no exception. One plausible alternative is being developed by a Irish software designer and free speech advocate
Ian Clarke who is developing a different version of the Internet known as FREENET. Some advocates have accused FREENET as building a dark-side version of the Internet which lies beyond the reach of law enforcement. FREENET has no corporate body that can be slapped with a court order. FREENET would consist of software that connects individual PCs in an ad hoc way over the Internet and the PCs user can pass files over the network and mask it's Internet users identity. The current main concerns of the private and public sector are identify theft and computer extortion.
Identity theft victims are easy prey if they surf the Internet feeling safe and secure. The Internet has become a top tool for those intent on causing chaos and crime. People who would not give out such sensitive information as bank account or credit card numbers, PIN numbers, and their social security number are falling to computer criminals known as phishers, hackers, and teenage kids or kiddy scripts. People also would not want their information known to others, such as a criminal record or financial history of bankruptcy, especially to an employer. While people would prefer to keep such criminal or financial records private, this information can be legally and easily obtained through public records. What the Internet does is that it amplifies the problem by providing a cheap form of searching for individual information. On the Internet, sensitive information and private information may fall into the same category where a individual search would provide both results. This type of scamming people in order to gather their sensitive information has led to a higher degree of crime in the form of online extortion. Sharon Lemon, head of the
National High Tech Crime Unit commented on this growing wave of computer crime, " It is the kind of criminal activity that gangsters used in the 1920's. Pay up or we will shut your business down, in this case, a company's web site." The extortion threat is simple. These people will flood your web site with enormous requests packets known as DDOD ( distributed denial of service ) which will flood a companies web server until it virtually shuts it down and users can no longer access the company web site. One tactic that is used in these DDOD attacks are done by individuals known as BOT MASTERS who have accessed thousands of computers, in business and home alike unknown to the computer's owner. A certain software program which is embedded in these zombie computers is then launched to attack a particular web site by flooding it with information until the server is so overloaded that it shuts down. These BOT NETS appeared in the early 1990s and their rapid growth has been attributed to the explosion of growth in the home owners use of broad band computers. Security director of QinetiQ, Tony Dyhouse stated, " These type of attacks began by targeting online gambling web sites. If the site's online betting is interrupted for hours, it can cost them millions in revenues." These attacks then expanded to online payment services and financial institutions. One company which had been attacked several times was the online payment site
PROTX. The threat was the same every time. If
PROTX didn't pay $10,000 then their site would be flooded and forced to be shut down. The attackers made good on their promise when PROTX. refused to be extorted and they launched their BOT DDOD attack.
PROTX is now one of the most secured sites on the Internet as it now spends $876,000 annually on computer security. While PROTX was adamant by not paying the black mail money, but many companies unfortunately do. Those companies who do succumb to this extortion, do not deliver the money stuffed in duffle bags. The money is electronically transferred and washed through a cascade of accounts.Other forms being used by computer criminals is hiding their identity by hiding their tracks by masking the requesting IP addresses through proxy servers.
In 2000, it use to be kids in their bedrooms typing in malicious code on their PC who wanted notoriety by exploiting their computer hacking skills to their online friends, but that has all changed. Today these BOT MASTERS are well funded organizations employed by criminal enterprises such as the Russian Mafia, Middle Eastern Gangs, and American Organized Crime syndicates. Others involved may be the very same online Security Companies who provide Internet security service to the same companies they attack. They can have their cake and eat it too as many American Corporations & their CEOs have been exposed in the last decade as nothing more than criminal enterprises themselves, as in ENRON and CEO Charles Keeting fiasco which left millions of American citizens penniless due to corporate greed. There are ways to help you protect yourself from identity theft according to some analysts by visiting online sites such as
Credit Report , and the three major credit reporting agencies online,
TransUnion,
Experian, and
Equifax. Let the consumer beware while visiting sites that seem credible as their is no doubt that certain individuals employed by these agencies may be criminals as well. Whom better to steal your identity than those who have access to your credit history and private information. Another precaution is alerting the credit reporting agencies by phone and request a Initial Fraud Alert on your record.
BRITAIN APPROVES NATIONAL IDENTITY CARD
2005 DECEMBER; U.K. Prime Minister Tony Blair announced the approval of biometrics identify cards in October 2005 after The House of Commons passed the proposal with a 309 to 284 votes. The identity cards will store a citizen's finger prints, iris scan, and facial recognition technology. The U.K. biometrics identity cards may set the global standard for all nations in which the global population will be marked and scanned and the biometrics information then stored in a global data base.
Japan's Big Brother 2005

Japanese Citizens Disguised as Human Bar Codes Protest Juki Net
2005 JULY: Yoshiaki Takashi, 68, one of millions of Japanese citizens is outraged at Japan's growing data base known as Juki Net, will store the names of Japanese citizens including their age, sex, data and city of birth. The Juki Net data base will also assign every japanese citizen a 11 digit bar code for identification. This governmental protocol was launched in 2002 and has already unleashed an unprecedented nationwide rebellion among the japanese citizens, whom are normally know for for their passiveness and trust of the government. " It's very rare that people are saying no to a national policy of Japan.", stated Seiji Mizunaga, a japanese legal representative. Many japanese citizens fear the future sinister developments of Juki Net and it's vulnerability to abuse by the police and government agencies. Mr. Takashi stated," I am furious at the men who want to know my private data when they have no business with such things. The government has given numbers to human beings as if we were animals." Juki Net will be the Japanese version of The US Patriot Act. The last six months has seen quite a global march to the ultimate Big Brother in that the global population will be nothing more than kilobytes of information in a global computer data base.. One can hope it can be stopped before it's to late, but that time has already passed. Below are recent articles from around the globe on the march to a New World Order where everyone will be monitored and marked like so many branded cattle being led to slaughter. The Japanese government's version of Big Brother is just the latest of events which have caught the citizen's attention. This article will be compacted to illustrate the march toward a global government. I have researched the latest technologies and global politics since 1996. In conclusion, make no mistake about it, the tracking and monitoring of human beings or storing people in a national or global data-base has nothing to do with terrorism, national security, or any other legal terminology, although they are used in those areas. The only purpose to store a countries population in a computer data-base is for control and monitoring human beings, regardless if they are called The Patriot Act, Juki Net, or a Social Security Number. BIG BROTHER IS WATCHING YOU! Below will be two articles named METHOD and Technology on how this Owellian horror is taking place.





 The United Nations Assembly Council can be seen as a form of The New World Order & One World Government
The United Nations Assembly Council can be seen as a form of The New World Order & One World Government



 Jacque Delors and, Past Current President Santer Jacques of The ECC which resides on the 13th floor of the Berlaymont, the enourmoud headquarters in Brussels Belgium.
Jacque Delors and, Past Current President Santer Jacques of The ECC which resides on the 13th floor of the Berlaymont, the enourmoud headquarters in Brussels Belgium.  European Common Market World Headquarters in Brussels Belgium
European Common Market World Headquarters in Brussels Belgium

 The Rebirth of The Roman Empire
The Rebirth of The Roman Empire

 This is the European flag. It is the symbol not only of the European Union but also of Europe's unity and identity in a wider sense. The circle of gold stars represents solidarity and harmony between the peoples of Europe. The number of stars has nothing to do with the number of Member States. There are twelve stars because the number twelve is traditionally the symbol of perfection, completeness and unity. The flag will therefore remain unchanged regardless of future EU enlargements. The history of the flag goes back to 1955. At that time, the European Union existed only in the form of the European Coal and Steel Community, with just six Member States. But a separate body with a larger membership, the Council of Europe, had been set up several years earlier and was busy defending human rights and promoting European culture. The Council of Europe was considering what symbol to adopt for its own use. After much discussion, the present design was adopted - a circle of twelve gold stars on a blue background. In various traditions, twelve is a symbolic number representing perfection. It is also, of course, the number of months in a year and the number of hours shown on a clock face. The circle is, among other things, a symbol of unity. So the European flag was born, representing the ideal of unity among the peoples of Europe. The Council of Europe then encouraged other European institutions to adopt the same flag and, in 1983, the European Parliament took up the call. Finally, in 1985, the flag was adopted by all EU heads of State and government as the official emblem of the European Union, which, in those days, was called the European Communities. All European institutions have been using it since the beginning of 1986.
This is the European flag. It is the symbol not only of the European Union but also of Europe's unity and identity in a wider sense. The circle of gold stars represents solidarity and harmony between the peoples of Europe. The number of stars has nothing to do with the number of Member States. There are twelve stars because the number twelve is traditionally the symbol of perfection, completeness and unity. The flag will therefore remain unchanged regardless of future EU enlargements. The history of the flag goes back to 1955. At that time, the European Union existed only in the form of the European Coal and Steel Community, with just six Member States. But a separate body with a larger membership, the Council of Europe, had been set up several years earlier and was busy defending human rights and promoting European culture. The Council of Europe was considering what symbol to adopt for its own use. After much discussion, the present design was adopted - a circle of twelve gold stars on a blue background. In various traditions, twelve is a symbolic number representing perfection. It is also, of course, the number of months in a year and the number of hours shown on a clock face. The circle is, among other things, a symbol of unity. So the European flag was born, representing the ideal of unity among the peoples of Europe. The Council of Europe then encouraged other European institutions to adopt the same flag and, in 1983, the European Parliament took up the call. Finally, in 1985, the flag was adopted by all EU heads of State and government as the official emblem of the European Union, which, in those days, was called the European Communities. All European institutions have been using it since the beginning of 1986.




 The Old North American Bar Code Above For More Information Visit
The Old North American Bar Code Above For More Information Visit 

 A Space Station or Big Brother's Future "Eye In The Sky"We have discussed the Global Satellite Positions (GPS) many times in our reporting. The United States "STAR WARS" defense against ICBMs launched against American soil is based on the theory of a space station or satellite that would use laser technology to blast these launched nuclear missiles in flight before they reach American soil. What I find interesting is if this program were deployed and it was successful, what what stop this same type of laser technology from blasting Global Satellite Positions from ground based facilities? Another troubling aspect is the explosion of a ICBM in the earth's atmosphere and the effects of nuclear fall out. The first employment of the STAR WARS defense element's system could be in place by 2004 beginning in Alaska as it's first deployment area. I find their is no winner in either scenario as I myself would rather be killed in a nuclear attack than live in a world as a survivor of a nuclear war. The Space Station which orbits our planet is a combined effort of several nations. This space station could easily be used much like the (GPS) in the tracking and monitoring everything to vehicles, people, livestock, and all forms of telecommunications. Former United States President Ronald Reagan's vision of STAR WARS may not be popular as to the building of some type of a missile defense system due to the fact that The Pentagon will undoubtedly use this technology for the deployment of offensive space satellite weapons. The United States is moving ahead with the Air Force's Airborne Laser program. The United States Air Force's Vision 2020 and the January 2001 Rumsfeld reports on the need of a space weapons defensive ( and offensive weapons no doubt. ) program are inevitable. Space war fare is a threatening and frightful aspect to human civilization, and will be a fact of life by the year 2015.
A Space Station or Big Brother's Future "Eye In The Sky"We have discussed the Global Satellite Positions (GPS) many times in our reporting. The United States "STAR WARS" defense against ICBMs launched against American soil is based on the theory of a space station or satellite that would use laser technology to blast these launched nuclear missiles in flight before they reach American soil. What I find interesting is if this program were deployed and it was successful, what what stop this same type of laser technology from blasting Global Satellite Positions from ground based facilities? Another troubling aspect is the explosion of a ICBM in the earth's atmosphere and the effects of nuclear fall out. The first employment of the STAR WARS defense element's system could be in place by 2004 beginning in Alaska as it's first deployment area. I find their is no winner in either scenario as I myself would rather be killed in a nuclear attack than live in a world as a survivor of a nuclear war. The Space Station which orbits our planet is a combined effort of several nations. This space station could easily be used much like the (GPS) in the tracking and monitoring everything to vehicles, people, livestock, and all forms of telecommunications. Former United States President Ronald Reagan's vision of STAR WARS may not be popular as to the building of some type of a missile defense system due to the fact that The Pentagon will undoubtedly use this technology for the deployment of offensive space satellite weapons. The United States is moving ahead with the Air Force's Airborne Laser program. The United States Air Force's Vision 2020 and the January 2001 Rumsfeld reports on the need of a space weapons defensive ( and offensive weapons no doubt. ) program are inevitable. Space war fare is a threatening and frightful aspect to human civilization, and will be a fact of life by the year 2015.  Japanese Citizens Disguised as Human Bar Codes Protest Juki Net
Japanese Citizens Disguised as Human Bar Codes Protest Juki Net
